Introducing Elastic Security 7.7.0
Editor’s Note — August 19, 2020: The Elastic Endpoint Security and Elastic SIEM solutions mentioned in this post are now referred to as Elastic Security. The broader Elastic Security solution delivers endpoint security, SIEM, threat hunting, cloud monitoring, and more.
We are excited to share the release of Elastic Security 7.7, which advances our goal of providing an open and free foundation for security practitioners everywhere to protect their organizations from hidden adversaries. This release broadens the availability of data within Elastic SIEM, builds on the power of Kibana alerting to further automate threat detection and response, and aligns the work of security practitioners with embedded case management and a new integration with ServiceNow ITSM.
The latest version of Elastic Security is available on our Elasticsearch Service on Elastic Cloud and as part of the Elastic Stack.
Let’s explore the highlights of Elastic Security 7.7.
Streamline response with built-in case management
Elastic Security 7.7 introduces embedded case management, streamlining incident response and reducing mean time to respond (MTTR). A new, built-in case workflow allows analysts to open, update, tag, comment on, close, and integrate cases with external systems. Upon detecting a threat and performing initial qualification, analysts can quickly create a case to organize known details and drive further action. This workflow thereby helps instill and streamline standard operating procedures related to triage, qualification, and escalation.
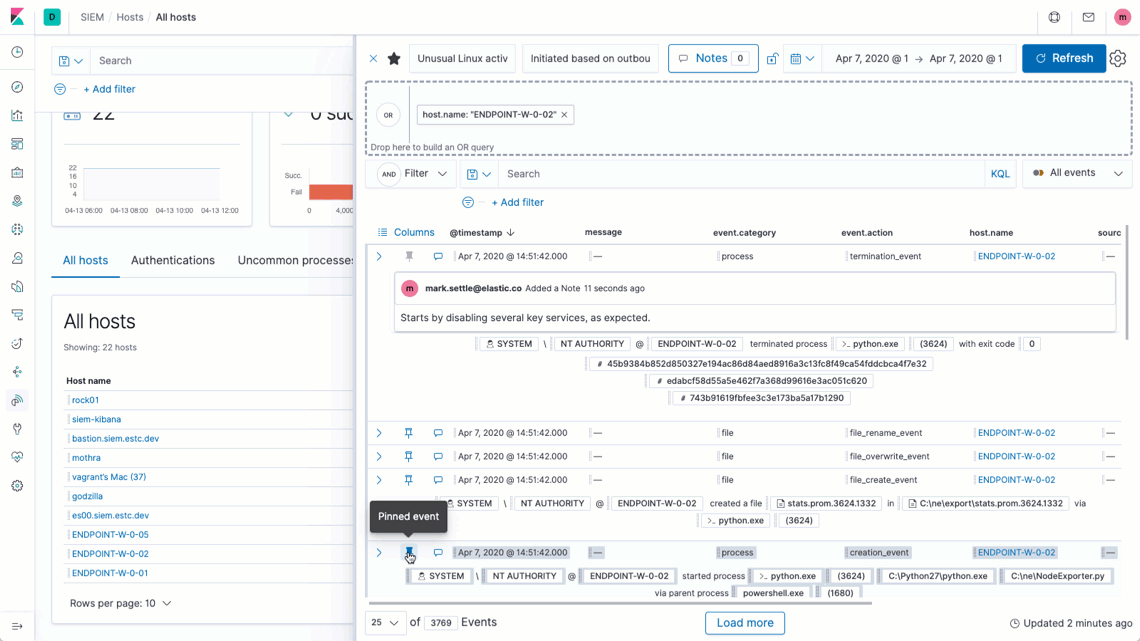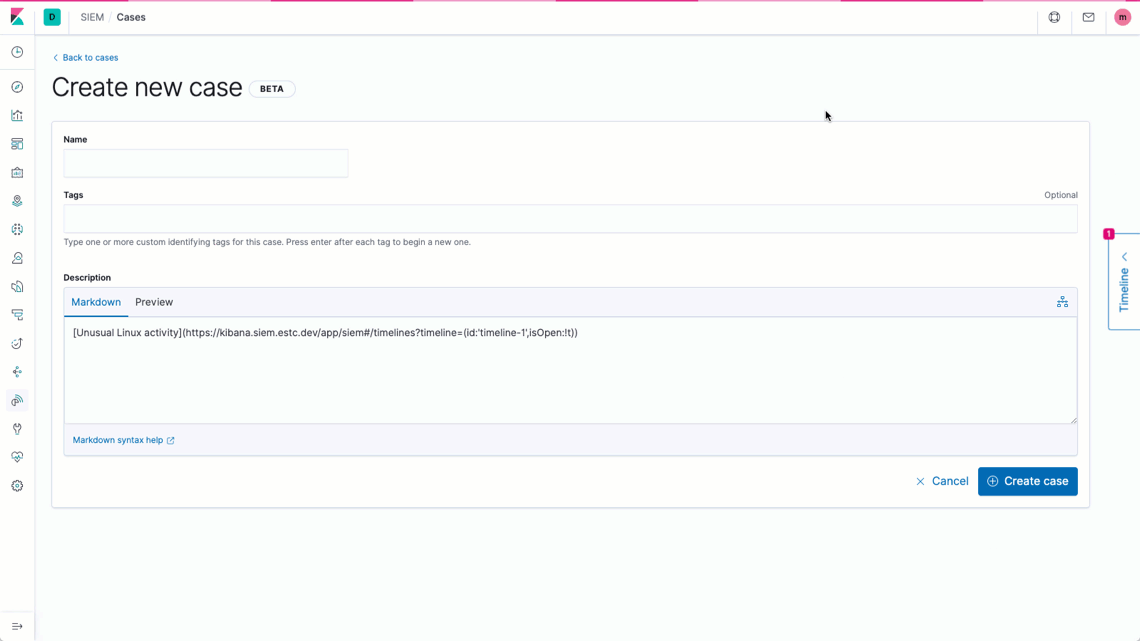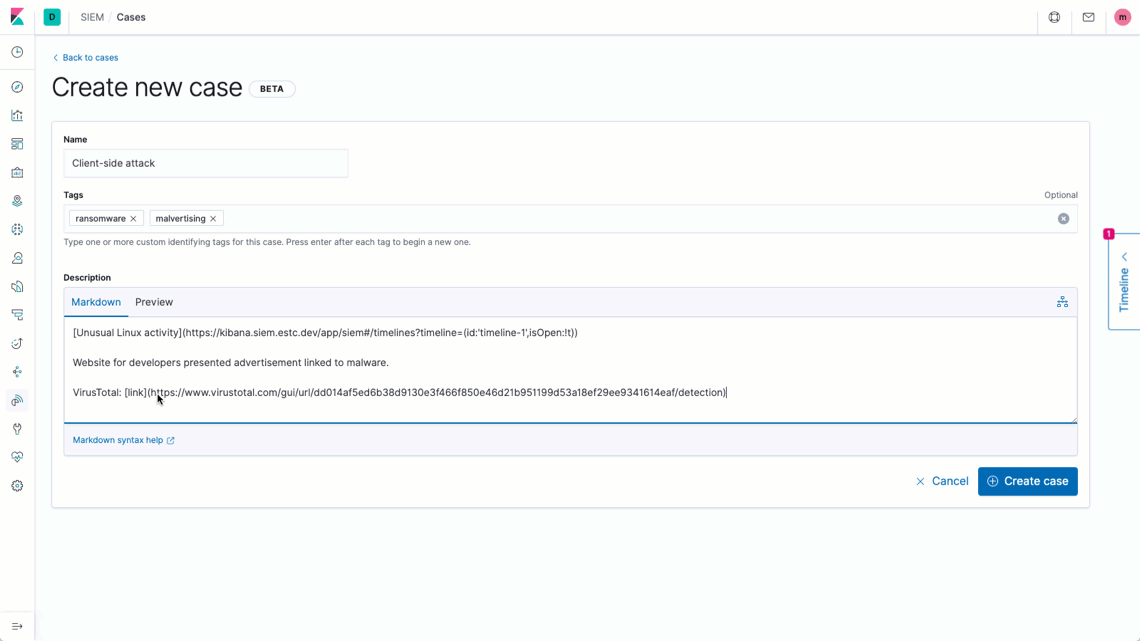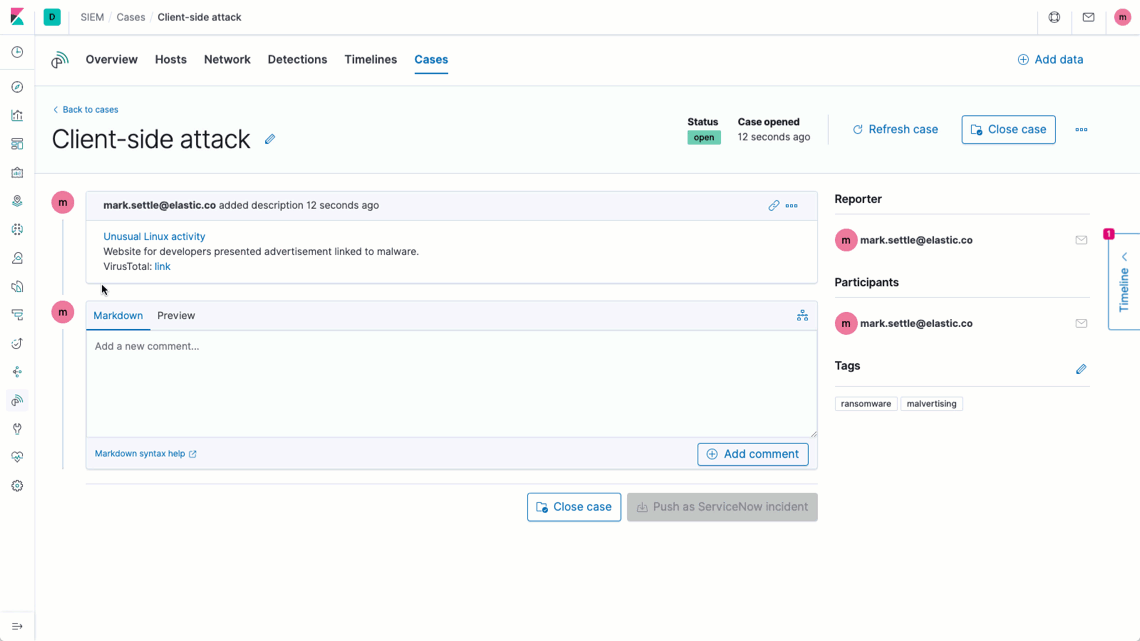 The new case management workflow in Elastic Security 7.7 facilitates tracking detection and response times for individual cases. Practitioners can also generate monitoring and security posture dashboards with visualizations showing MTTR and related metrics, such as case open duration and open vs. closed ratio.
Investigation guide playbooks can now be included within SIEM detection rules through rich markdown fields that enable rule writers to deliver contextual resources to security analysts. Investigation guide fields provide a place for remediation recommendations, checklists, reference information, and any other details that might be relevant to an analyst opening a related detection signal.
The new case management workflow in Elastic Security 7.7 facilitates tracking detection and response times for individual cases. Practitioners can also generate monitoring and security posture dashboards with visualizations showing MTTR and related metrics, such as case open duration and open vs. closed ratio.
Investigation guide playbooks can now be included within SIEM detection rules through rich markdown fields that enable rule writers to deliver contextual resources to security analysts. Investigation guide fields provide a place for remediation recommendations, checklists, reference information, and any other details that might be relevant to an analyst opening a related detection signal.
To facilitate collaboration, Elastic SIEM 7.7 enables the sharing of investigation timelines both within the organization and across the greater security community via a simple export and import function.
Coordinate response with a native integration between Elastic SIEM and ServiceNow ITSM
Elastic’s new case management function is directly integrated with ServiceNow IT Service Management (ITSM), improving coordination and alignment within (and beyond) the security operations team. The integration allows analysts to forward investigative findings from Elastic SIEM to the ServiceNow platform, ensuring clear hand-offs, automating key steps, and enabling tracking across the incident lifecycle. Analysts need to be able to operate with the most up-to-date information, so the native connector supports ad-hoc updates.
Configuring the integration between Elastic SIEM and ServiceNow ITSM is remarkably simple. Does your organization use a different third-party system for ticketing, orchestration and automation, or incident response? Dig into our open API for Elastic SIEM case management.
Surface key anomalies and threats with instant notifications from Elastic SIEM to third-party systems
Elastic Security 7.7 reduces MTTR with a new alerting feature and new ways to combine machine learning jobs and detection rules. Together, these enhancements bring responders into the loop without delay.
To help analysts and other stakeholders respond quickly, a new alerting feature allows practitioners to configure any SIEM detection [rule] to instantly inform third-party systems of new SIEM detection signals. Built-in connectors to email, Slack, PagerDuty, and generic webhooks enable implementation with a wide array of customer environments. A new “actions” field on individual SIEM detection rules enables granular configuration of notifications to one or more third-party tools.
 Machine learning anomalies can now be analyzed by the SIEM detection engine, enabling immediate surfacing of anomalies that could indicate threats like web shells and compromised accounts. SIEM detection rules triggering the execution of machine learning-based anomaly detection jobs and generating detection signals in the event of high-scoring anomalies can also now be implemented. This capability offers the accuracy of targeted analytical methods and the simplicity of a unified rule administration experience. All of the prebuilt machine learning jobs delivered with Elastic Security now leverage this capability.
The SIEM rule detail page provides expanded access to the data that security engineers need to tune detection content effectively. Opening an individual rule reveals how often it fires and when, how often it is associated with an open or closed case, and how long it takes to run.
Machine learning anomalies can now be analyzed by the SIEM detection engine, enabling immediate surfacing of anomalies that could indicate threats like web shells and compromised accounts. SIEM detection rules triggering the execution of machine learning-based anomaly detection jobs and generating detection signals in the event of high-scoring anomalies can also now be implemented. This capability offers the accuracy of targeted analytical methods and the simplicity of a unified rule administration experience. All of the prebuilt machine learning jobs delivered with Elastic Security now leverage this capability.
The SIEM rule detail page provides expanded access to the data that security engineers need to tune detection content effectively. Opening an individual rule reveals how often it fires and when, how often it is associated with an open or closed case, and how long it takes to run.
More data, more visibility, more protection
Version 7.7 further helps organizations eliminate blind spots by collecting new sources of cloud, application, and security data. We’ve expanded out-of-the-box data source support with new Filebeat modules for Okta and Microsoft 365 (previously called Office 365) and an expansion of the Filebeat CEF module for Check Point. Okta data enables the analysis of cloud application and infrastructure access. Microsoft 365 data provides deep visibility into cloud application usage. Check Point network data enables global detection. Updated operating system support deepens access to host and system information within Elastic SIEM.
Expanded out-of-the-box protections for Elastic Security
Elastic Security 7.7 enhances the out-of-the-box protection capabilities delivered by Elastic SIEM and Elastic Endpoint Security — and makes several related improvements, too.
 To equip organizations to address the latest security threats at scale, Elastic security experts continue enhancing our out-of-the-box machine learning jobs and rules to address the latest security threats. This prebuilt content equips security programs to automate protection.
To equip organizations to address the latest security threats at scale, Elastic security experts continue enhancing our out-of-the-box machine learning jobs and rules to address the latest security threats. This prebuilt content equips security programs to automate protection.
Elastic SIEM 7.7 provides new prebuilt detection rules protecting against:
- Living-off-the-land techniques — attackers using executing malicious code with OS-native applications (which are typically vendor-signed) to bypass app whitelisting-based defenses
- Privilege escalation via UAC bypass and related techniques — attackers bypassing Windows User Account Controls (UAC) with elevated permissions or leveraging application permissions to load malicious DLLs
- Suspicious child processes of targeted business applications — attackers using PDF applications to download and execute malicious payloads
One more thing: Wherever you use Elastic SIEM — whether in a home lab or as part of an enterprise SOC — these prebuilt rules are open and free, ready for adoption.
Get started today
Want to give Elastic SIEM a spin? Experience our latest version on Elasticsearch Service on Elastic Cloud or try an Elastic SIEM demo. Already have ECS-formatted data format in Elasticsearch? Just upgrade to 7.7 of the Elastic Stack to start detecting and responding.
Want to attend an Elastic{ON} Tour virtual event and get free registration? Choose an upcoming session.