From raw data to real-time defense: A conversation with John Hammond
Explore how Elastic Security's unified platform with SIEM and XDR protections transforms SOC workflows through AI-powered analytics and consolidated security operations.
.png)
Elastic Security Director of Product Management James Spiteri recently joined cybersecurity researcher, educator, and content creator John Hammond for an in-depth technical demonstration. John spends his days analyzing malware, breaking down attacker techniques, and making hackers earn their access.
In their conversation, James and John explored how SOC teams are detecting threats faster, investigating more efficiently, and responding to incidents in real time. They also take a hands-on look at how Elastic Security transforms security teams’ raw data into actionable intelligence and automation through AI-assisted data ingestion, analysis, automated triage, and streamlined incident response.
Open, accessible, enterprise-grade protection
In the video, we explore how Elastic is rethinking endpoint security. Traditional EDR tools have grown increasingly complex with fragmented capabilities and escalating costs that put advanced protections out of reach for many organizations.
Elastic takes a different approach — security that is open, transparent, and accessible by design. Installing the Elastic Agent is a single command, immediately enabling free, enterprise-grade malware protections powered by open YARA signatures. Ransomware defenses go beyond detection to active safeguards, such as file heuristics, canary files, and MBR protections, while behavioral rules continuously look for suspicious activity sequences on the endpoint.
But prevention alone isn’t enough. Elastic turns raw telemetry into actionable insight through investigation tools like process tree view, which presents a graphical timeline of processes before and after an alert and allows analysts to drill into related hosts, processes, and events. Complementing this is session view, which organizes Linux process data into an intuitive, terminal-inspired format based on parentage and execution time. This enables teams to monitor session activity and understand user and service behavior at a glance. The result is a future-proof model for endpoint security — open where others are closed; integrated where others are siloed; and designed to make world-class protection available to every security team, not just those with unlimited budgets.
AI-powered triage that combats alert fatigue
While the average enterprise SOC generates thousands of alerts daily, most teams investigate only a fraction due to resource constraints. Alert fatigue means important threats are missed while analysts burn out on false positives.
As demonstrated in the video, Elastic Security's Attack Discovery feature uses large language models (LLMs) to perform first-pass triage analysis, distilling potential attack campaigns from hundreds (or thousands) of individual alerts and providing chronological event sequences with affected hosts and users.
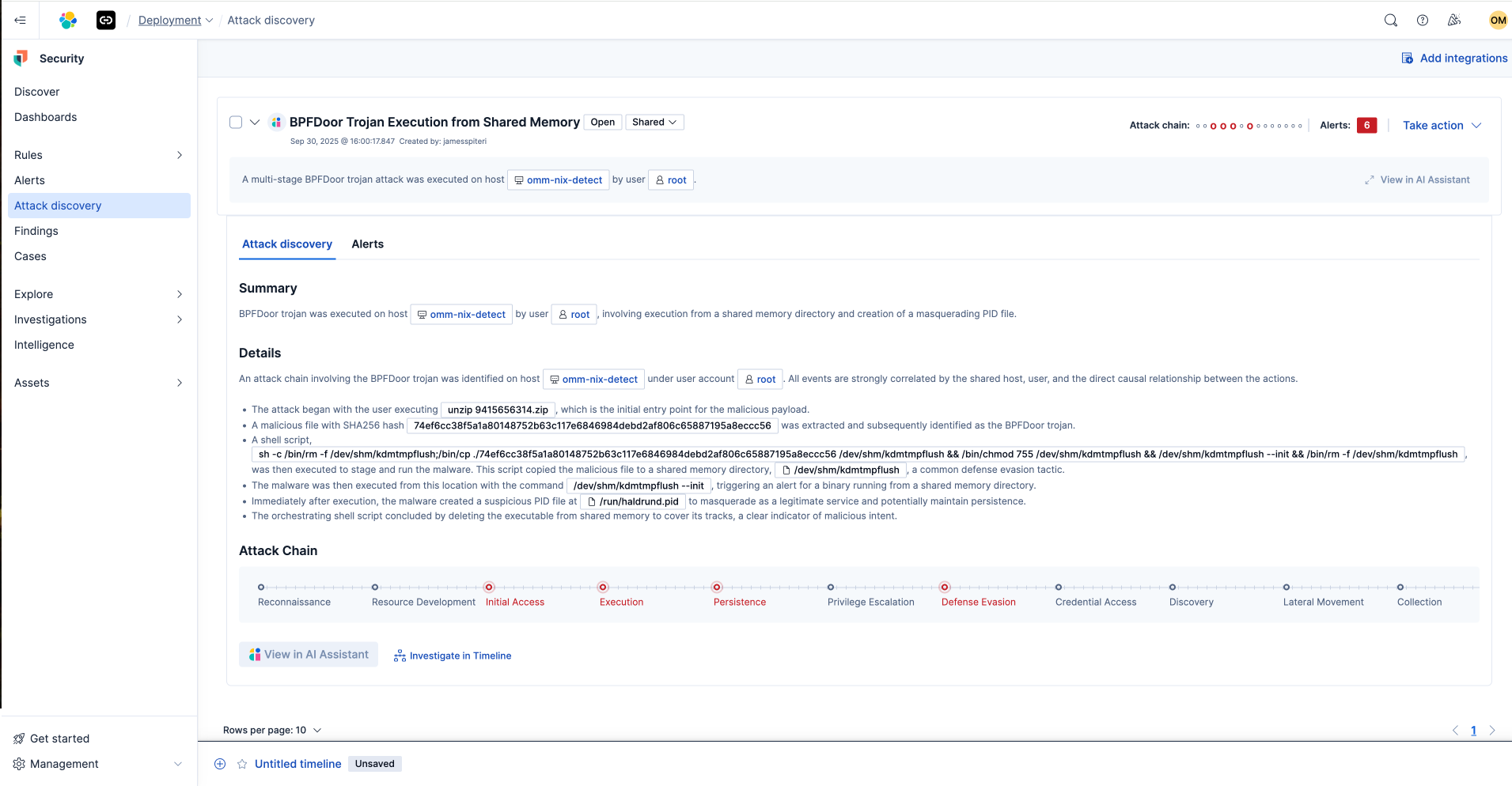
This capability dramatically accelerates mean time to detect (MTTD) by providing immediate, actionable summaries for even the most complex, multistage attacks. Analysts retain control over their preferred LLM selection, including open source options while gaining transparency into underlying data and logic.
To further combat alert fatigue, Elastic AI Assistant enables natural language queries on alerts and retrieval of remediation guidance relevant to specific incidents. For advanced hunting, Elastic integrates LLMs directly within Elasticsearch Query Language (ES|QL) queries, allowing analysts to score obfuscated PowerShell scripts and receive plain language descriptions of malicious intent — transforming manual analysis into automated, scalable hunting.
Converging tool sprawl
Security architectures typically require multiple agents and collectors, creating deployment complexity and coverage gaps. This approach also forces analysts to switch between different tools during critical incident response.
Elastic consolidates data collection into a single Elastic Agent with 400+ prebuilt integrations, handling parsing and normalization automatically. For a manual deployment, the user only needs to copy and execute a single command line. From there, the script installs the Elastic Agent and applies the preconfigured policy, which automatically begins collecting and consolidating all the required data sources as defined in the policy's integrations.
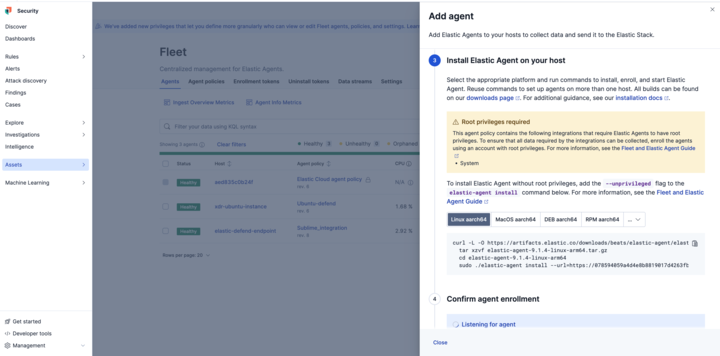
For enterprise teams managing thousands of endpoints, this operational efficiency eliminates administrative overhead that typically consumes significant SOC resources.
See how central management allows simultaneous updates across all endpoints, freeing analysts to focus on threat hunting rather than infrastructure management.
Breaking free from black box detection
Many security platforms treat detection logic as proprietary, leaving analysts unable to understand why alerts trigger or how to optimize rules for their environment. This opacity reduces confidence in detections and further contributes to alert fatigue.
Elastic Security provides nearly 1,500 detection rules with all logic publicly available in a GitHub repository. This allows analysts to easily inspect rule code, contribute improvements, and learn advanced detection techniques. Elastic's open source foundation delivers complete transparency in security detection logic — no black boxes or hidden algorithms.
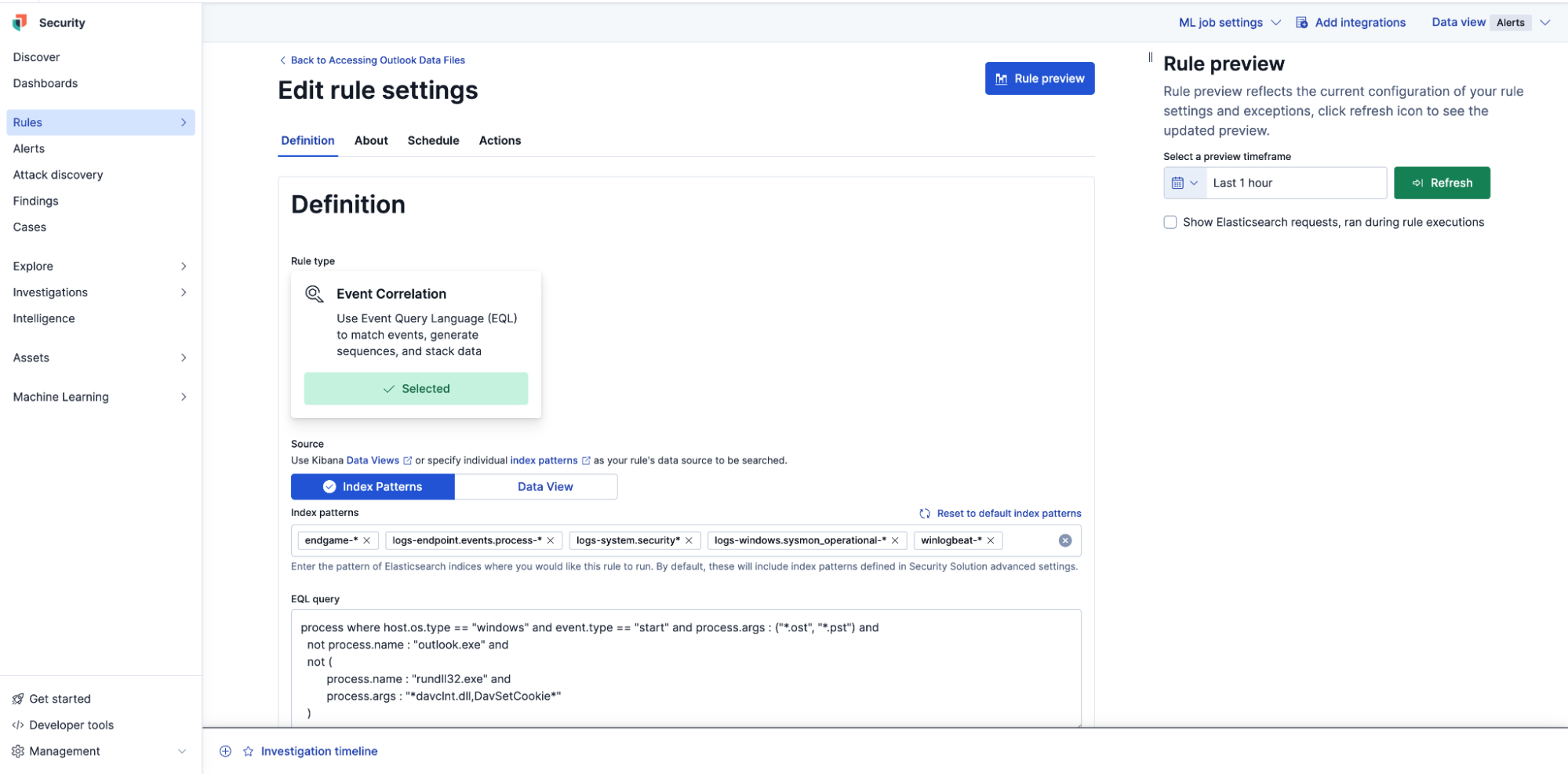
Unified response across all platforms
Traditional incident response requires switching between different tools for different platforms, slowing response times and increasing the risk of procedural errors during high-stress situations.
Elastic Security provides a unified response console across Windows, macOS, and Linux. In the video, James shows real-time host isolation, process termination, and forensic file retrieval — all from a single interface. These actions extend to third-party endpoints, including endpoints managed by CrowdStrike, SentinelOne, and Microsoft Defender, while maintaining complete audit histories essential for compliance and post-incident analysis.
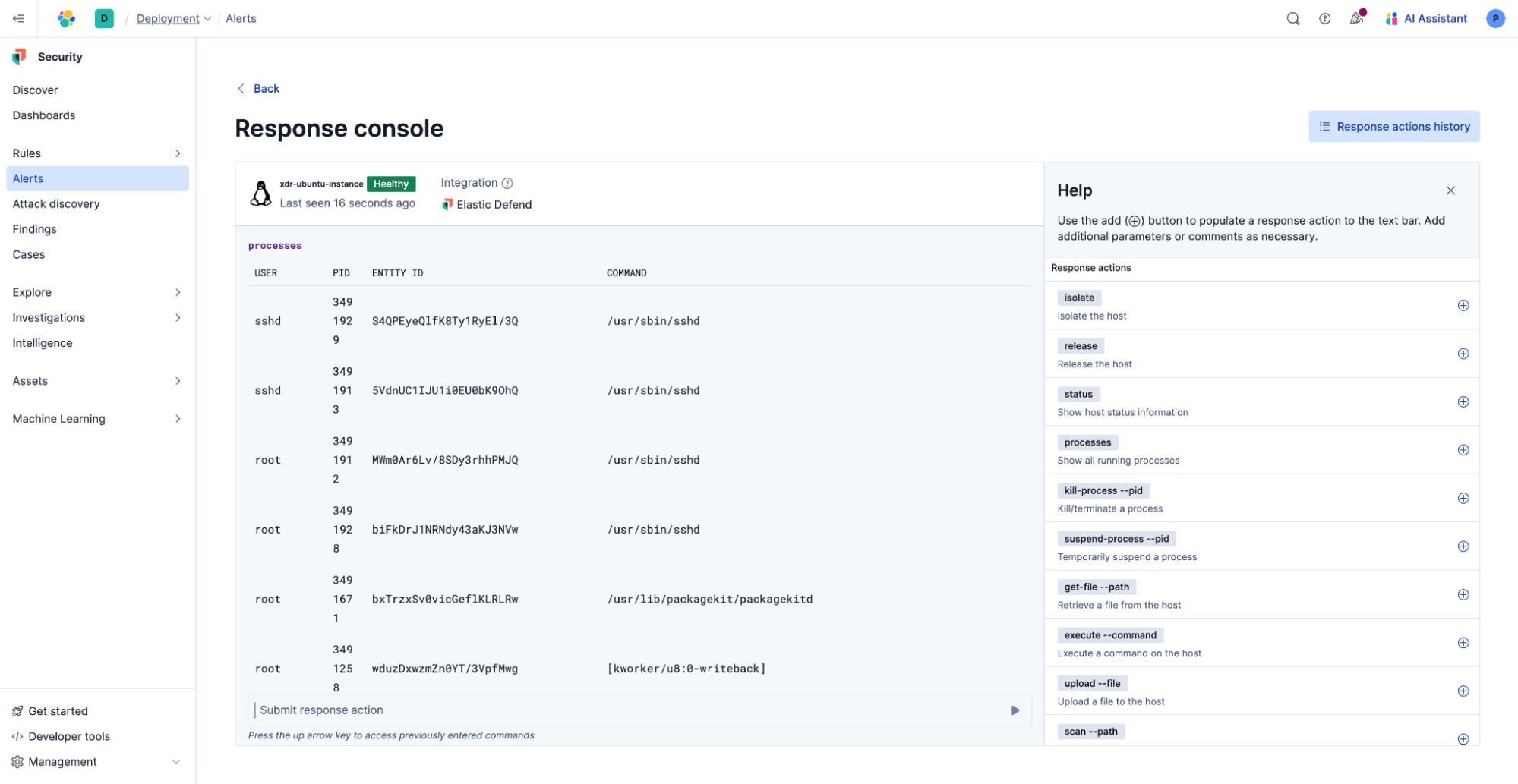
This unified response eliminates tool switching during active incidents, reducing cognitive load on analysts while ensuring consistent procedures and proper documentation.
Experience Elastic Security yourself
The Elastic Security product overview demonstrates how comprehensive security analytics can be delivered through a single, AI-enhanced platform. This approach covers everything from data ingestion to threat hunting to incident response without teams sacrificing capability or flexibility.
For security teams evaluating their current architecture, the question isn't whether individual point solutions work but instead whether fragmented approaches can keep pace with sophisticated threats and growing data volumes. Elastic's unified platform offers consolidated visibility, accelerated analysis, and streamlined response while maintaining the transparency and flexibility that security professionals demand.
Ready to experience unified security analytics for the AI era? Deploy your own Elastic Security instance today.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.