IMPORTANT: No additional bug fixes or documentation updates will be released for this version.
Overview
editOverviewedit
SIEM enables analysis of host-related and network-related security events as part of alert investigations or interactive threat hunting.
The SIEM app in Kibana provides an interactive workspace for security teams to triage events and perform initial investigations. Additionally, machine learning anomaly detection jobs and detection engine rules provide ways to automatically detect suspicious activity across your entire fleet of servers and workstations.
SIEM componentsedit
SIEM requires the following Elastic Stack components.
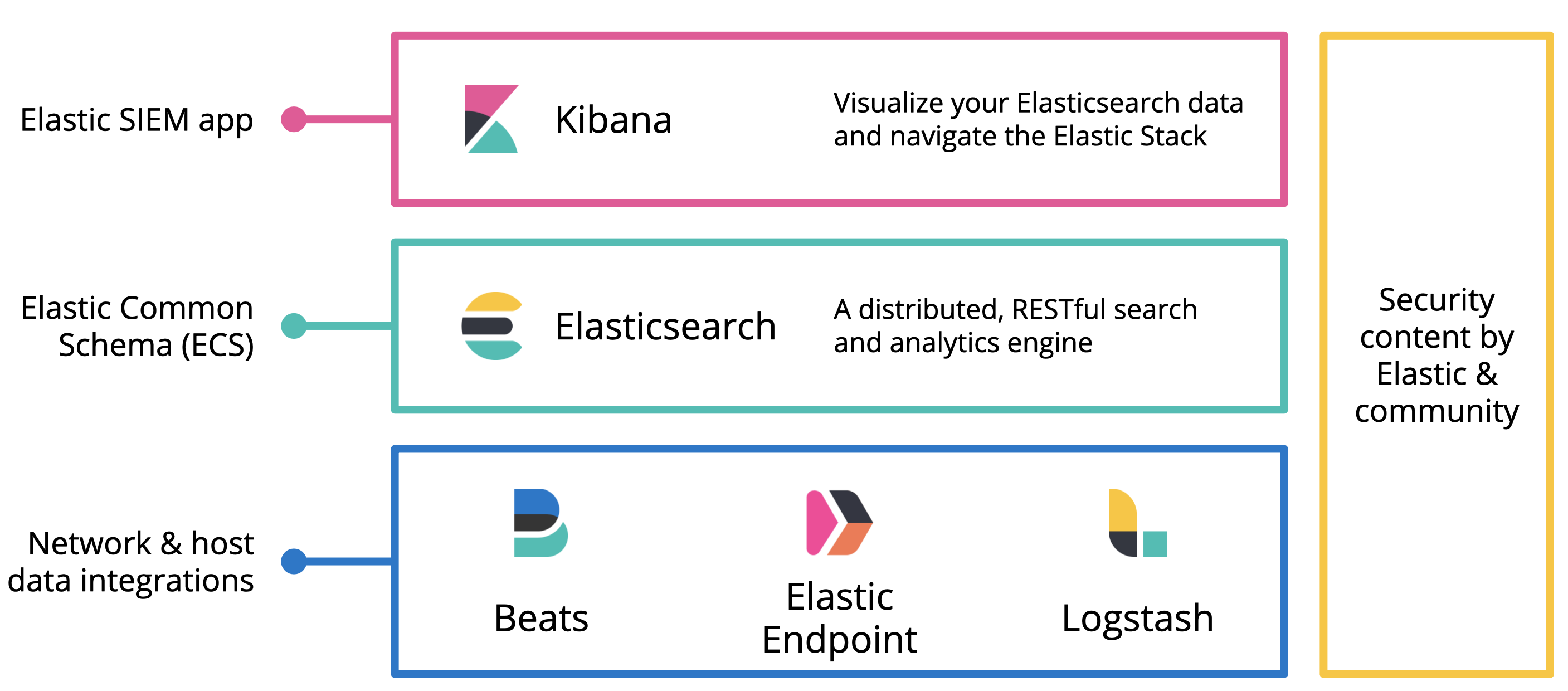
Elastic Endpoint Security is an endpoint security platform and agent that provides prevention, detection, and response capabilities. It ships events and security alerts directly to Elasticsearch.
Beats are open source data shippers that you install as agents on your systems. Beats send security events and other data to Elasticsearch.
Elasticsearch is a real-time, distributed storage, search, and analytics engine. Elasticsearch excels at indexing streams of semi-structured data, such as logs or metrics.
Kibana is an open source analytics and visualization platform designed to work with Elasticsearch. You use Kibana to search, view, and interact with data stored in Elasticsearch indices. You can easily perform advanced data analysis and visualize your data in a variety of charts, tables, and maps.
Additional Elastic componentsedit
You can use SIEM with other Elastic products and features to help you identify and investigate suspicious activity:
Data sourcesedit
SIEM can ingest and analyze data from a variety of sources, including Elastic Endpoint Security, Beats and Beats modules, APM transactions, and third-party collectors mapped to the Elastic Common Schema (ECS).
Hosts data sourcesedit
-
-
System module - Linux, macOS, Win
- packages
- processes
- logins
- sockets
- users and groups
- Auditd module (Linux Kernel Audit info)
- File integrity module (FIM) - Linux, macOS, Win
-
-
- system logs (auth logs) - Linux
- Santa - macOS
-
- Windows event logs - Windows
Network data sourcesedit
-
- Flows
- DNS
- other protocols
Elastic Endpoint Sensor Management Platformedit
The Sensor Management Platform (SMP) ships all relevant host and network data directly to the SIEM app.
APM transactionsedit
By default, the SIEM app monitors APM
apm-*-transaction* indices. To add additional APM indices, update the
index patterns in the siem:defaultIndex setting (Kibana → Management →
Advanced Settings → siem:defaultIndex).
Elastic Common Schema (ECS) for normalizing dataedit
The Elastic Common Schema (ECS) defines a common set of fields to be used for storing event data in Elasticsearch. ECS helps users normalize their event data to better analyze, visualize, and correlate the data represented in their events.
SIEM can ingest and normalize events from ECS-compatible data sources.
Host identificationedit
All Beats use the add_host_metadata processor to add the host.name field to
events. The default value is host.name, but you can change it in Beats
processor settings.