What’s new in 8.7
editWhat’s new in 8.7
editHere are the highlights of what’s new and improved in Elastic Security. For detailed information about this release, check out the Release notes.
Other versions: 8.6 | 8.5 | 8.4 | 8.3 | 8.2 | 8.1 | 8.0 | 7.17 | 7.16 | 7.15 | 7.14 | 7.13 | 7.12 | 7.11 | 7.10 | 7.9
Detection rules enhancements
editRules table UX enhancements
Several improvements were made to the Rules table:
- Advanced sorting is now enabled by default, allowing you to sort the table by any column without changing any settings.
- When filters are active, a Clear filters button now appears to help quickly remove all filters.
- Filters and sorting now persist after you navigate away from and back to the page until you remove them manually. They also persist when you share the page URL.
- There is now a dedicated Enabled rules / Disabled rules button to quickly view only enabled or disabled rules.
Alert suppression time window for custom query rules
You can now suppress custom query rule alerts during a specific time window to limit alert volume and reduce alert noise. Duplicate alerts within that time window will be grouped.
Connectors can be exported and imported with rules
Now, when you export and import a rule that uses action connectors, you don’t need to handle the connectors separately. Note that sensitive information about the connector (such as authentication credentials) is not included in the export file. You must re-add missing connector details after importing detection rules.
Cross-cluster search support for indicator match rules
You can now query data in remote clusters and cold-tier data using index patterns specified in indicator match rules.
Enhancements to rule preview
You can now resize the Rule preview panel.
New Torq connector for rule actions
There’s a new Torq connector you can select when configuring rule actions. You must have at least a Platinum subscription to use this connector.
Exceptions enhancements
There are several enhancements and UI improvements to rule exceptions:
- When adding a rule exception, you can make it temporary by setting an expiration date and time. You can view active and expired exceptions under the Rule exceptions tab and choose whether to include expired exceptions when exporting rules.
-
If a field has mapping conflicts, it has a warning icon (
 ) and message that describes the conflicts. You can use this information to prevent exception errors and resolve mapping problems.
) and message that describes the conflicts. You can use this information to prevent exception errors and resolve mapping problems.
- The Manage rules button has been renamed to Link rules, and the Import list button has been renamed to Import value list.
Machine learning job enhancements
Machine learning job names now appear instead of job IDs throughout the Elastic Security app so you can quickly know which Machine learning jobs you’re interacting with.
Prebuilt rule updates
Check out the latest updates to prebuilt rules. To download the latest updates, refer to Download latest Elastic prebuilt rules.
New integrations
editThe following security integrations have been added in 8.7:
- AuditD
- Content Delivery Network
- Credential Management
- Database
- EDR/XDR
- Email Security
- Firewall
- Identity & Access Management
- Threat Intelligence
- Vulnerability Management
The Integrations page also has improved categorization and search functionality.
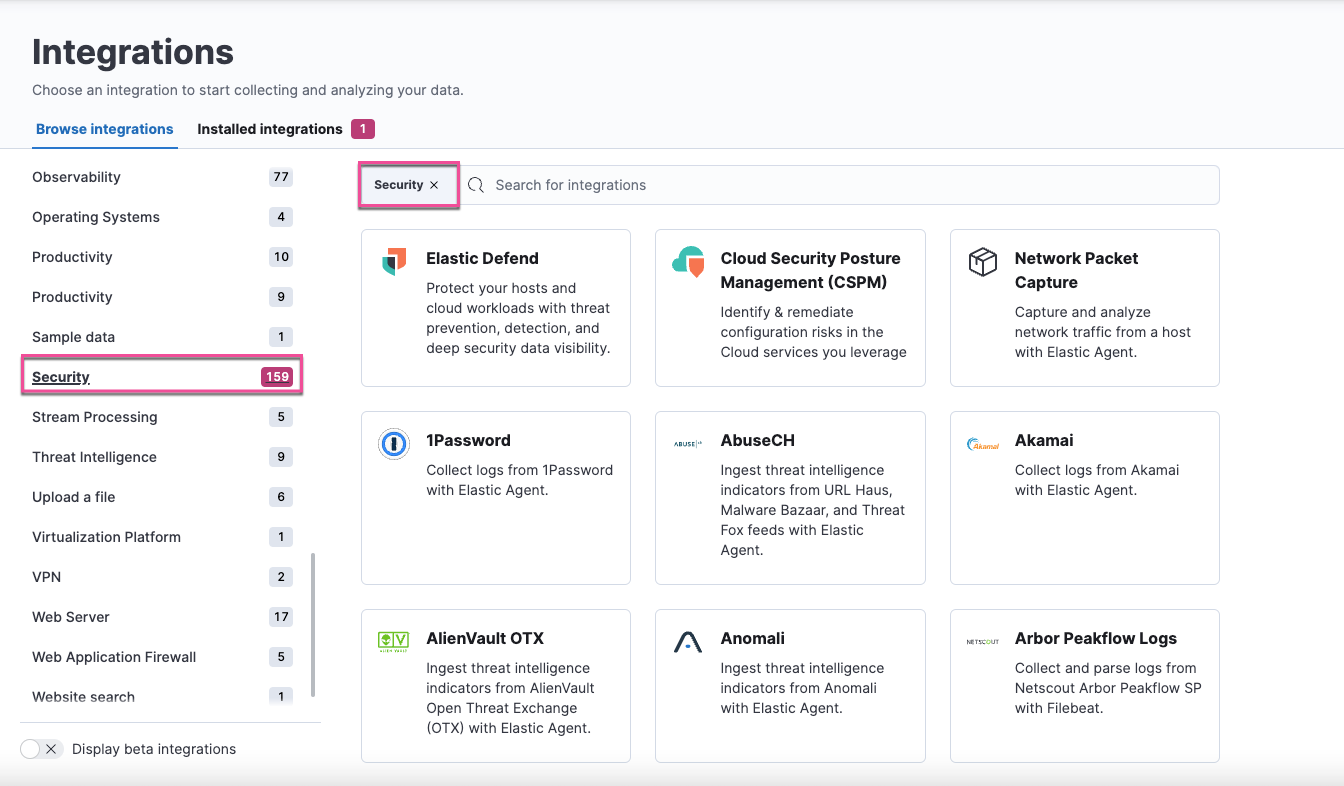
Role-based access control (RBAC) for response actions
editNew Endpoint management feature privileges in Kibana allow admins to have more granular control over Elastic Defend features. Role-based access can now be managed for the following:
- Hosts running Elastic Defend
- Trusted applications
- Host isolation exceptions
- Blocklist entries
- Event filters
- Elastic Defend policies
- File-related operations in the response console
Response console action enhancements
editA new get file response console action allows you to retrieve and download a file from a host. Files are downloaded in a password-protected .zip archive to prevent them from running.
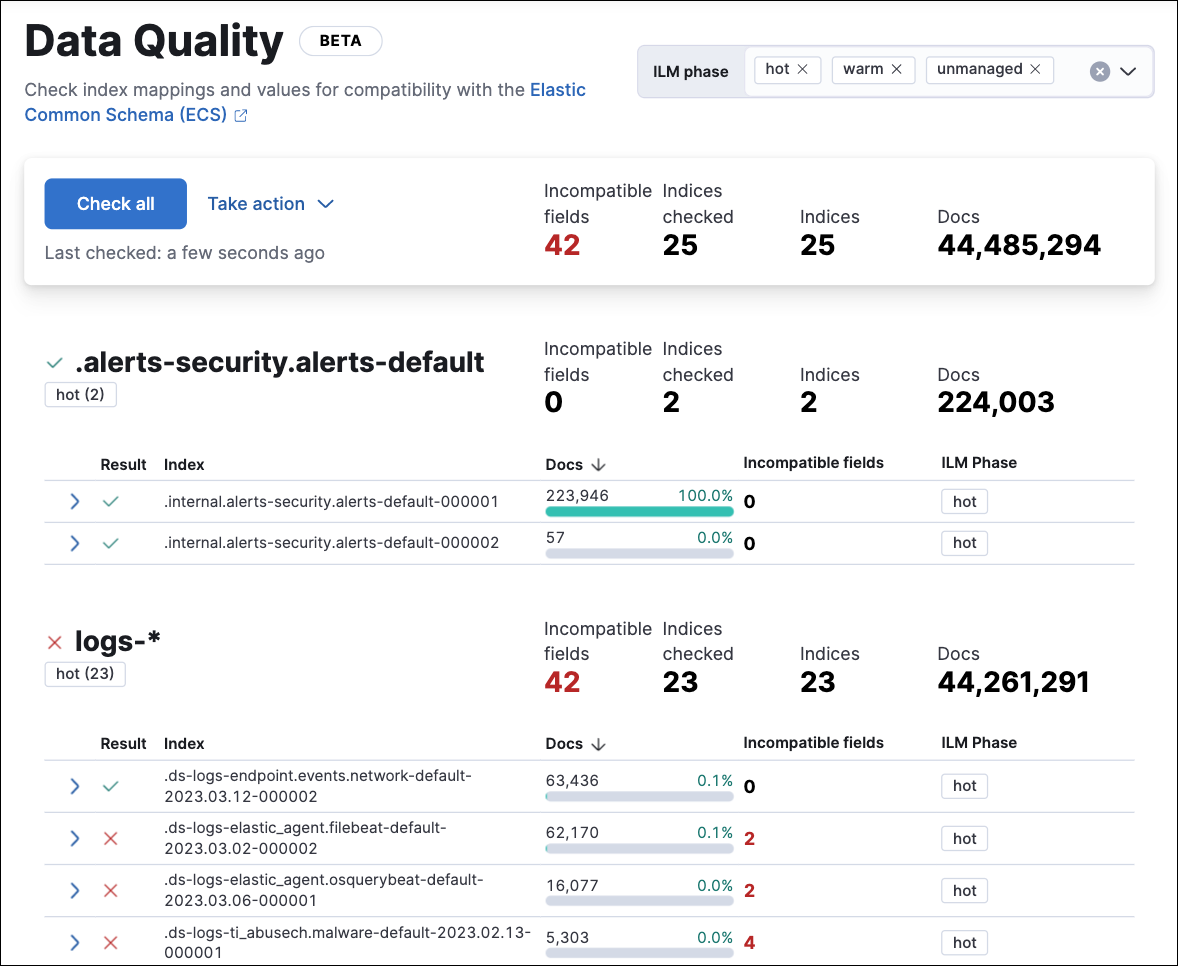
Data Quality dashboard
editThe Data Quality dashboard allows you to quickly check one or several indices for unmapped fields or fields with mapping conflicts, and makes it easy to track and share the results.
Alerts enhancements
editSummary visualization for key performance indicators (KPIs)
The new summary visualization on the Alerts page shows how alerts are distributed across severity levels, rule names, and specified fields such as host.name. You can hover and click on elements within the summary to add filters with those values to the Alerts page.
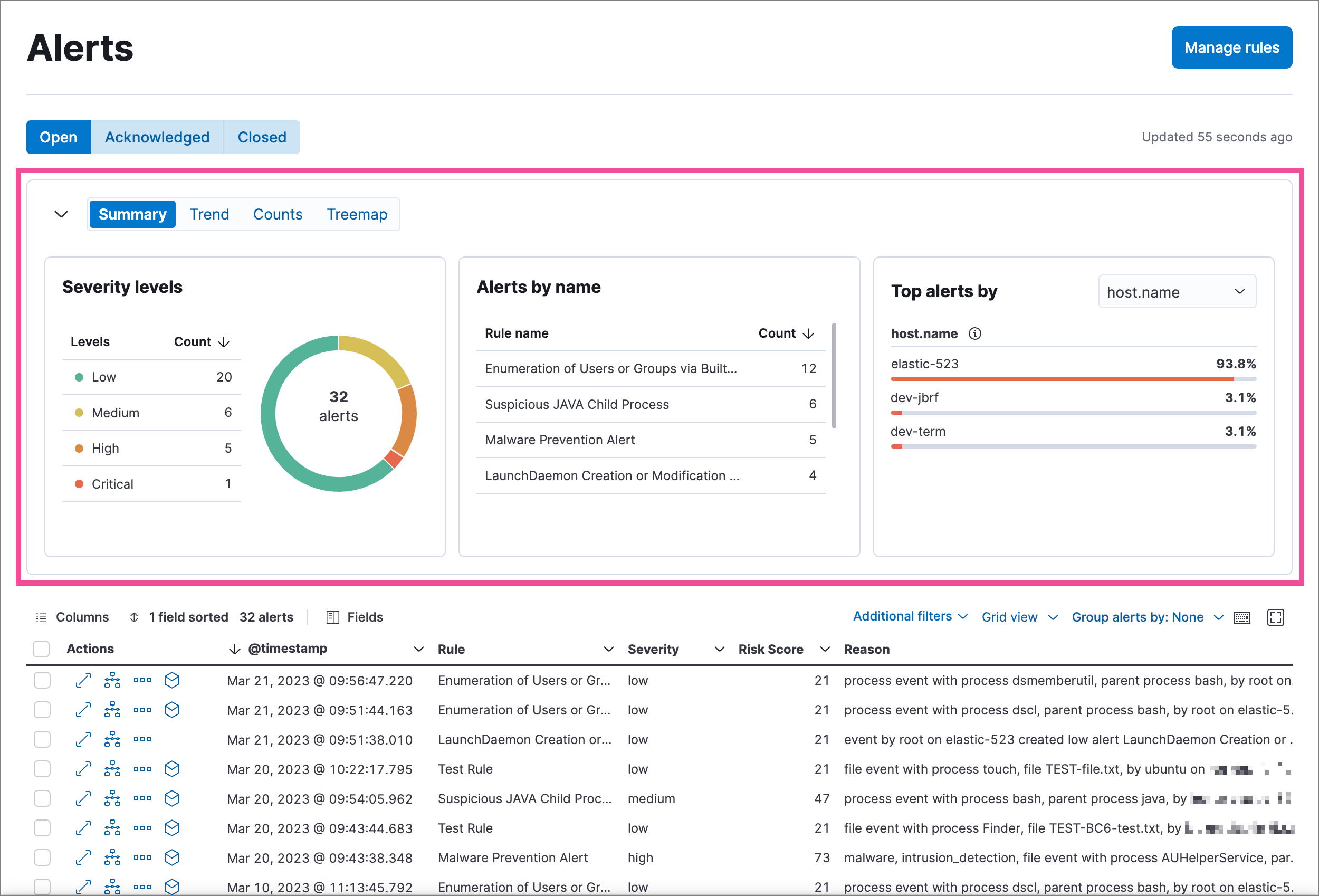
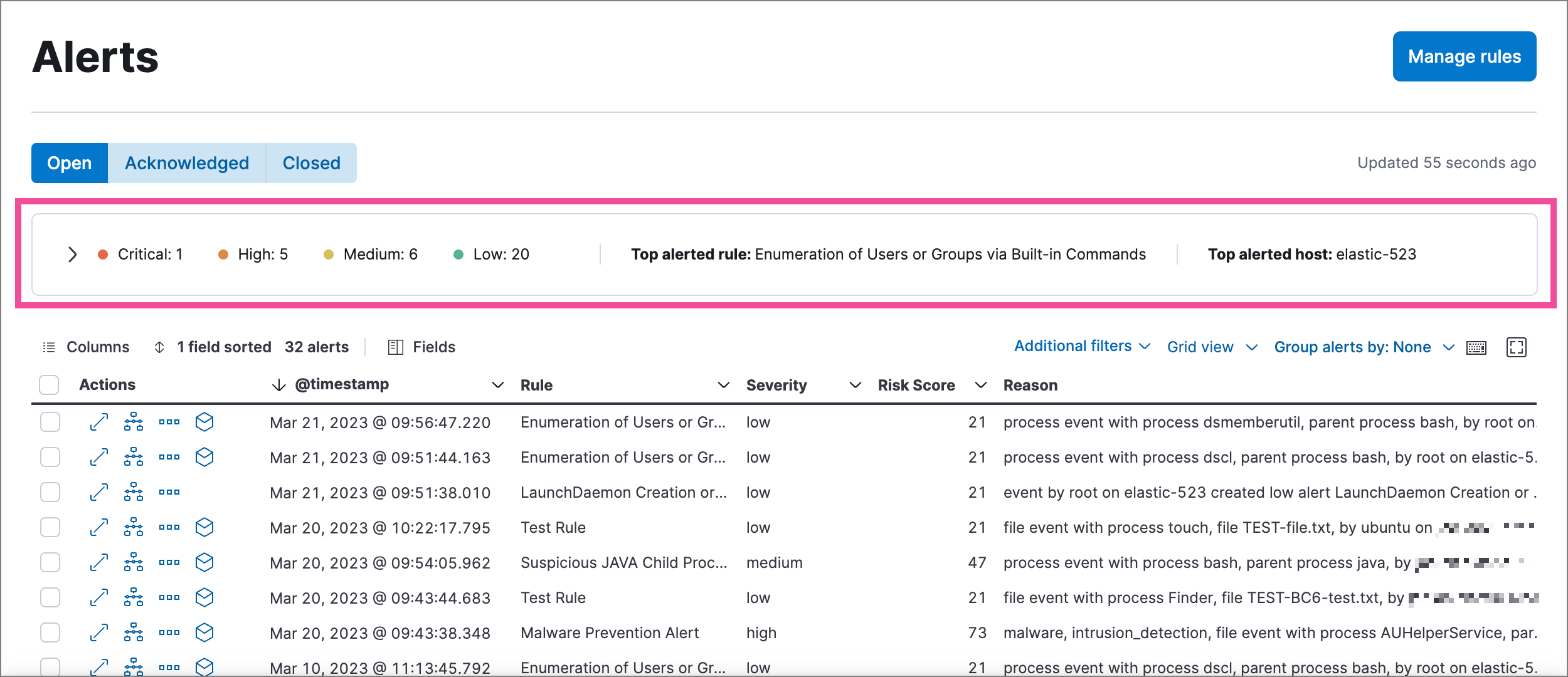
You can also minimize the visualization section to display a summary of key information instead.
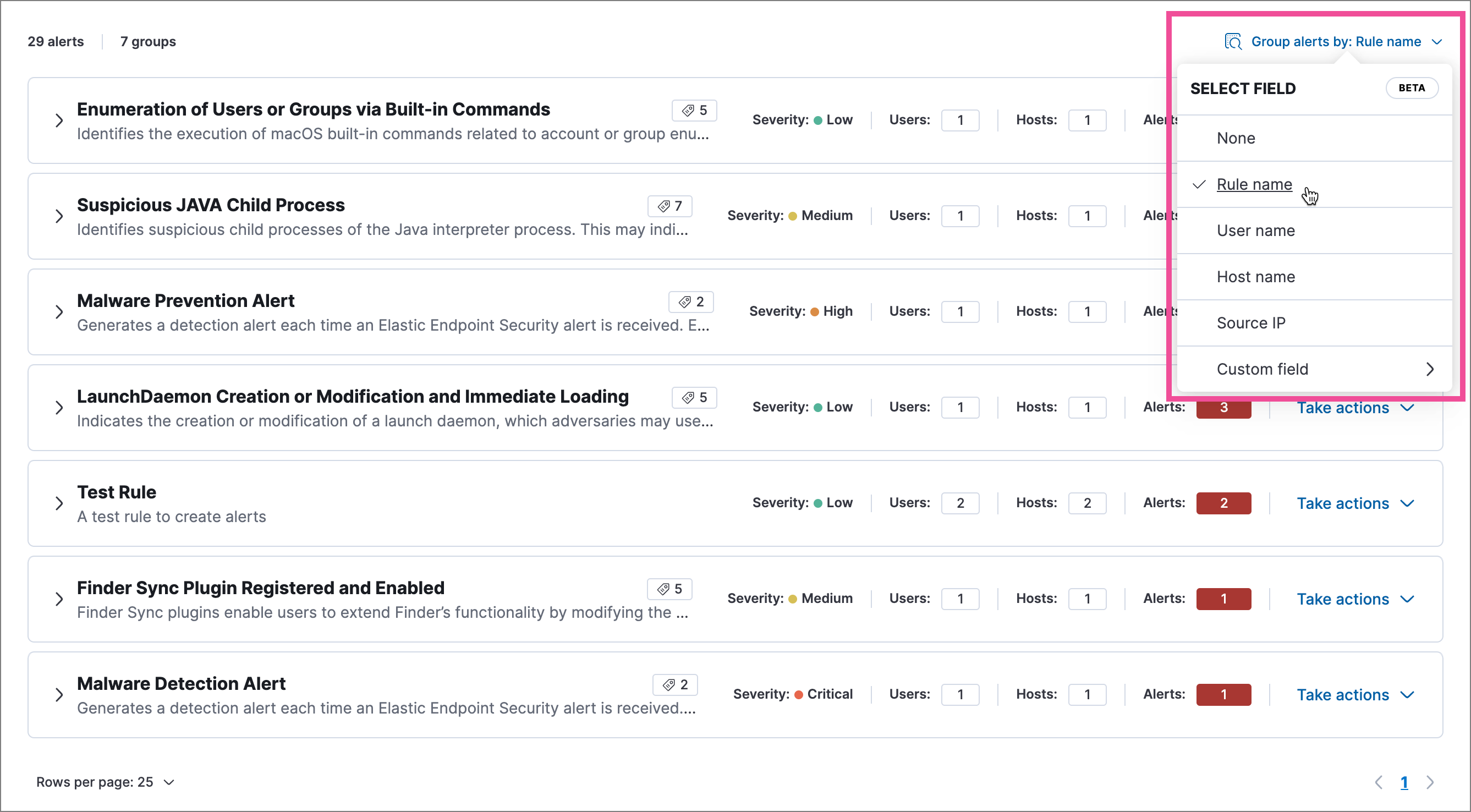
Alert grouping
Now in beta, this feature allows you to group alerts by rule name, host name, user name, source IP address, or any other field. Each group displays information such as the alerts' severity and how many users, hosts, and alerts are in the group, and you can expand a group to display its alerts.
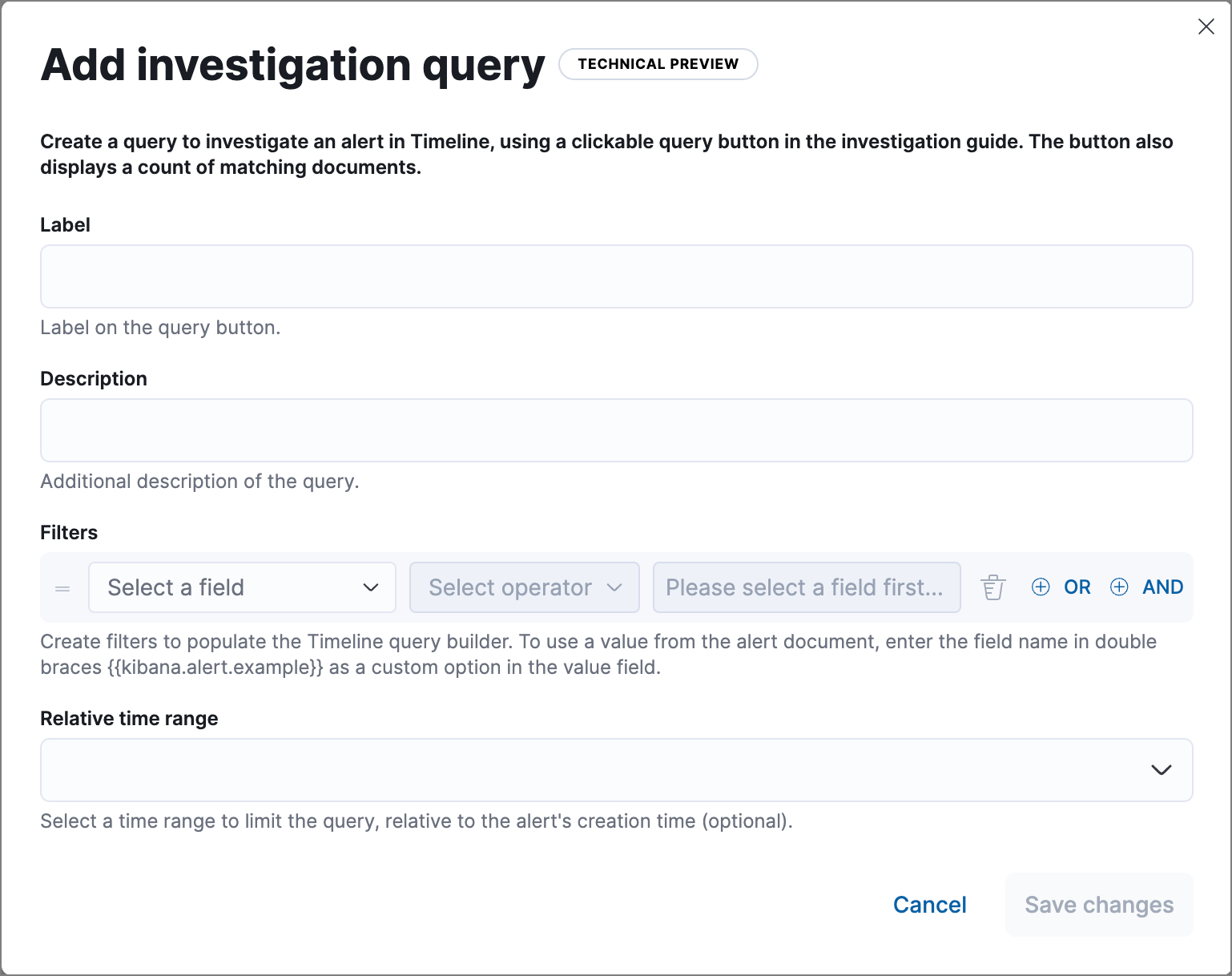
Interactive investigation guides query builder UI
editThe new query builder UI makes it easier to configure Interactive investigation guides (a technical preview feature introduced in 8.6). When you use it to create filters and build an investigation query, syntax is automatically added to the investigation guide editor, rendered as a clickable action button that launches the query in Timeline.
Cloud Security Posture enhancements
editCloud Security Posture Management (CSPM)
The new CSPM feature identifies security risks in your AWS account configuration by checking your infrastructure — including storage, compute, IAM, and more — against configuration security guidelines defined by the Center for Internet Security (CIS).
Threat intelligence enhancements
editBlock hashes and malicious files
You can now add indicator values to the blocklist to prevent selected applications from running on your hosts. You can use MD5, SHA-1, or SHA-256 hash values from file type indicators.
Improvements to indicators
There are several enhancements and UI improvements to indicators:
-
When you investigate an indicator in Timeline, the query’s time range is set to seven days before and after the indicator’s
timestamp. - You can now delete values entered into the Stack by field in the Trend chart.
-
When you open the Indicator table’s field browser, the
agent,base, andeventfield categories are preselected to narrow the scope of relevant fields. - The Indicator details flyout now has the Overview and Table tabs when you open indicator details from a case comment.
Cases enhancements
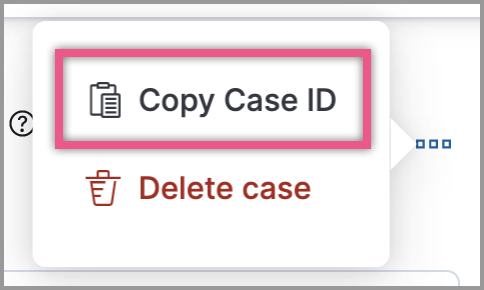
editCases can be shared
Each case now has a universal unique identifier (UUID) that you can copy and share. You can access a case’s UUID from the Cases page or the case details page.
Enhancements to cases
Several changes have been made to the Cases table to improve usability:
- Now you can bulk edit assignees.
- The new Updated on column shows the last time cases were modified.
- The Status, Severity, and Name columns are sortable.
- Any filters and sorting you apply to the table persist in the browser.
Osquery enhancements
editEvent and alert data can be dynamically transferred into Osquery queries
Instead of hard-coding alert and event values into Osquery queries, you can now use placeholder fields to dynamically pass this data into queries. Placeholder fields function like parameters and can be used to build flexible and reusable queries.
Add Osquery queries from a rule’s investigation guide to Osquery Response Action
Now, if a rule uses an Osquery query in its investigation guide, you can quickly add the query to the rule’s Osquery Response Action when editing it.
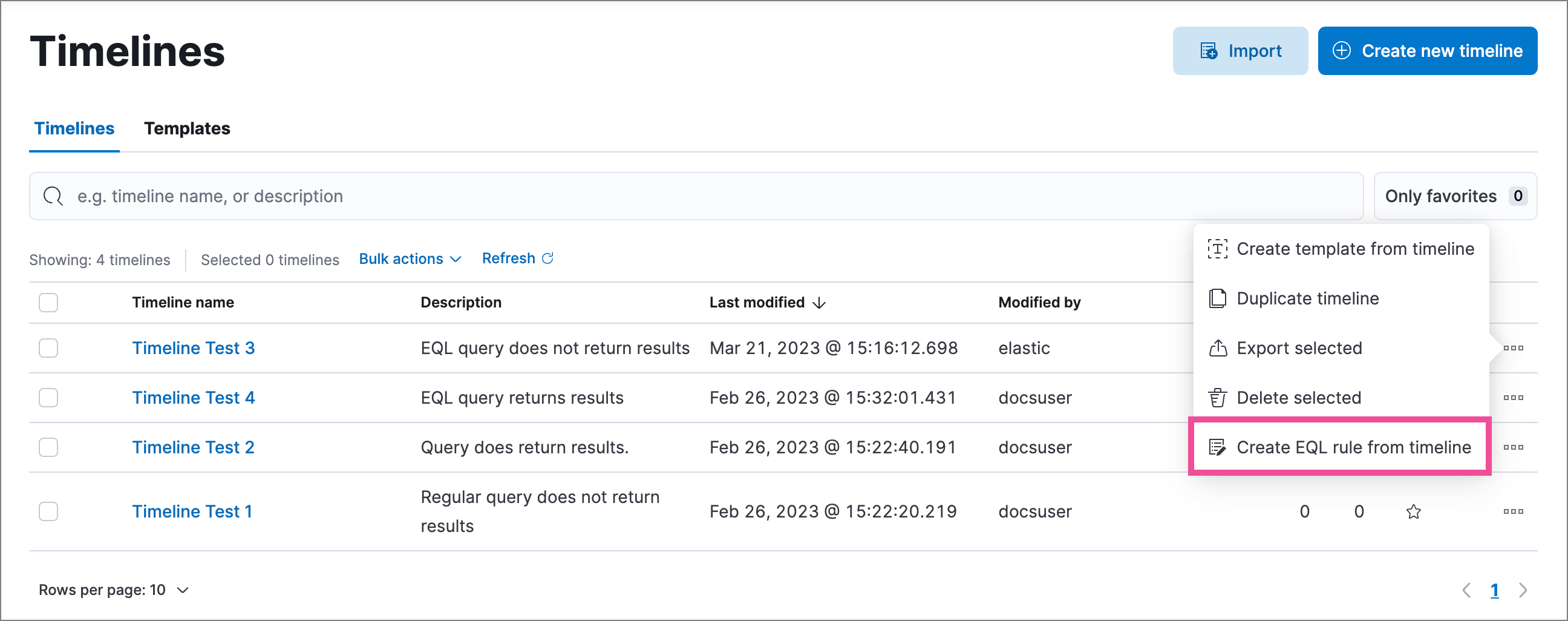
Create rules from Timelines
editIf a saved Timeline contains a KQL or EQL query, a new option in the Timelines page allows you to create a detection rule using that query. For example, to create an event correlation rule from a Timeline that includes an EQL query.