Elastic named a Leader in the IDC MarketScape: Worldwide Extended Detection and Response Software 2025 Vendor Assessment

We’re excited to announce that Elastic has been recognized as a Leader in the IDC MarketScape: Worldwide Extended Detection and Response Software 2025 Vendor Assessment (doc #US52997325, September 2025). We believe the IDC MarketScape’s recognition reflects Elastic’s strength in delivering agentic AI-driven, open, and unified SIEM and XDR at scale. Elastic Security helps organizations detect, investigate, and respond to threats without lock-in or limits.
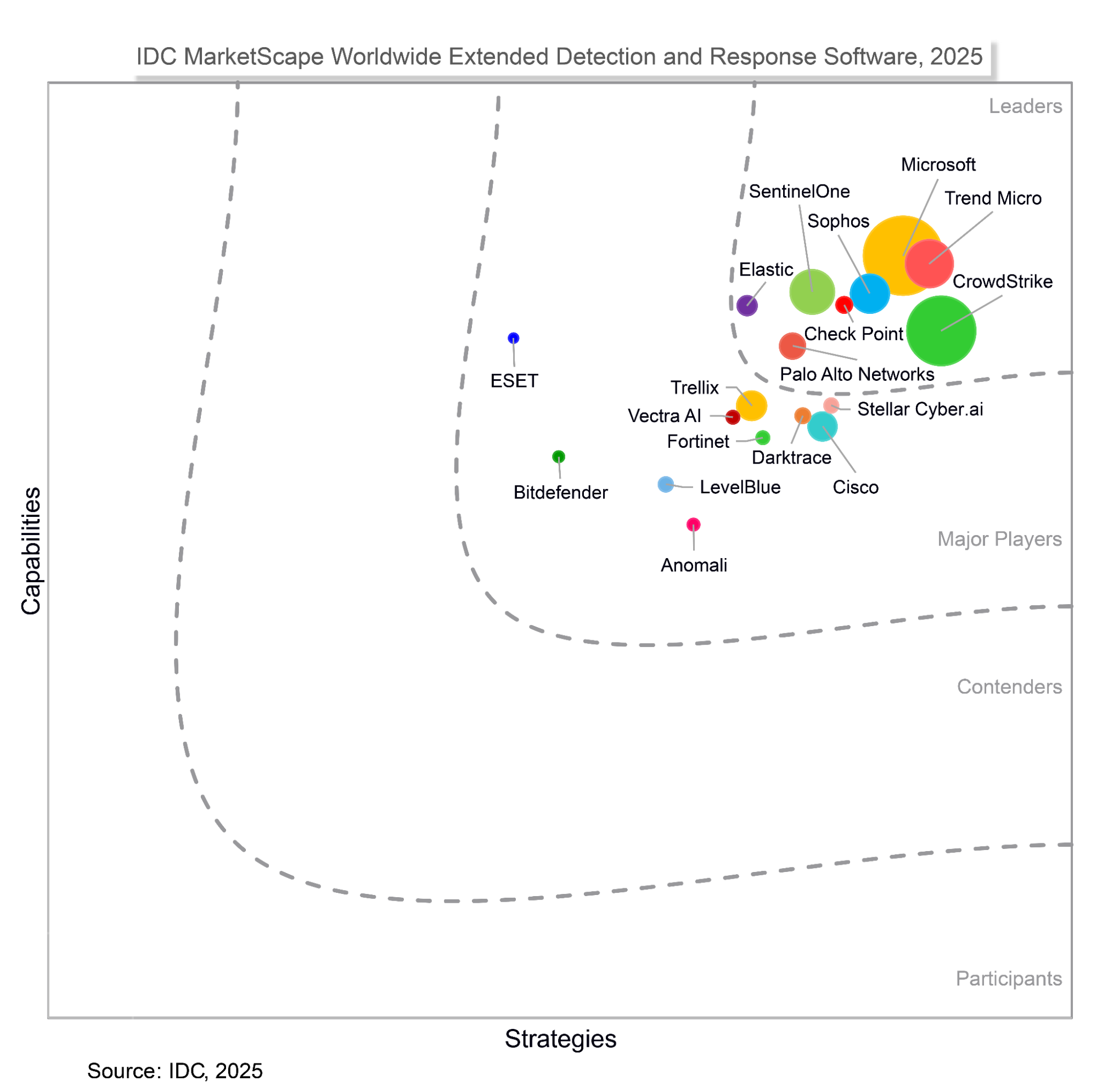
Why IDC MarketScape recognized Elastic as a Leader in XDR
Elastic was recognized for the following strengths:
Elastic has strong search and federated search capabilities. Invariably, a central strength of Elastic is its search capabilities. Two important differentiating features about Elastic in search are that its query is performed in real time through Osquery when data is ingested, and Elastic performs search where the data is.
- All capabilities in Elastic Security are included in the license. All of Elastic's capabilities are in the Elastic Security platform. User behavioral analytics, integrated threat intelligence, endpoint protection, cloud detection and response, and the use of a digital assistant are included at no additional cost.
- Elastic Defend provides countermeasures. Elastic Defend provides real-time behavioral analytics, deception techniques, and active prevention controls. Against ransomware, Elastic will monitor the endpoint for rapid file encryption, suspicious process spawning, and file system tampering.
- Elastic Security offers advanced digital assistant capabilities. A small thing that made IDC grin during the product demonstration phase was that IDC asked vendors to show an initial access screen and what a security analyst should investigate first. Elastic showed this, but then also said, "... you can also simply ask the Digital assistant what to investigate first."
Why we believe Elastic is an XDR Leader
Today, no organization runs on just one host, one operating system, or one type of device. You’ve got Windows laptops, Kubernetes clusters, Surface devices, and cloud workloads all generating signals at the edge. The edge itself has become a commodity.
What matters is context — the ability to unify all those edges into one platform where you can see, detect, and respond without compromise. That’s exactly what Elastic delivers: any edge, any signal, unified into full context. And when coverage gaps appear, our included endpoint closes them with proven protection. Unify the edge — don’t compromise on context. Elastic Security fulfills this through:
Critical context from AI-powered assistance and Attack Discovery: Attack Discovery acts like a virtual SOC analyst, correlating alerts, attack paths, and enterprise knowledge with RAG-based context to guide faster investigations. Meanwhile, the built-in Elastic AI Assistant integrates relevant environmental context to summarize, explain, and recommend next steps.
- A thoughtful approach to data ingestion: Elastic offers 400+ out-of-the-box integrations for popular data sources and supports data ingestion through syslog, APIs, files, cloud object storage (e.g., Amazon S3, Azure Blob), and custom Elastic Agent or Logstash configurations.
- An open and extensible platform: Elastic believes security should be open and transparent. We share our detections publicly, make our AI decisions explainable, and integrate seamlessly with third-party EDR vendors. Whether you choose Elastic Defend, another EDR, or both, Elastic Security unifies your data without forcing you into a single-vendor stack — giving you the freedom to enable XDR your way.
Analysts, testers, and practitioners agree: The verdict on Elastic Security
We believe the IDC MarketScape’s recognition highlights what security teams need most today: faster prevention, context-driven response, and less tool sprawl. With Elastic Security, threats are disrupted early, detection engineers have instant access to all their data, and analysts work from one unified platform instead of juggling fragmented tools.
But this recognition as a Leader for Elastic Security is far from an isolated event. From acing rigorous malware assessments to dazzling hardened security practitioners, Elastic Security is impressing all corners of the cybersecurity ecosystem.
Elastic Security’s early threat identification and prevention are regularly validated in AV-Comparatives Business Security Tests. In these AV-Comparatives tests, Elastic was the only vendor among 17 participants to achieve perfect 100% scores in both Malware and Real-World Protection across 220 complex attack simulations and 1,018 newly identified malware samples. Building on that success, in AV-Comparatives’ Endpoint Prevention and Response (EPR) annual report, Elastic outscored top competitors like CrowdStrike, Palo Alto Networks, and Fortinet in detecting 50 real-world advanced persistent threat (APT) scenarios, all while delivering equal or lower total cost of ownership.
But Elastic Security isn’t just getting noticed in the analyst community. Cybersecurity practitioners are giving Elastic cachet, too. Hacker, researcher, and content creator extraordinaire John Hammond recently took a hands-on look at Elastic Security. He was captivated with Elastic Security’s native AI capabilities like calling LLMs during threat hunting to quickly identify additional context that drastically improves even the most experienced security analysts’ time to detection.
Unified SIEM/XDR/cloud security and real-world threat research
The IDC MarketScape noted, “XDR is at an inflection point. The adversary works at the speed of AI and businesses expand their IT profile horizontally for new ways to deliver applications and store data. XDR is changing with this, and strategies need to evolve.”
Elastic Security Labs underpins our XDR leadership with continuously evolving, actionable threat research. Our investigations into advanced intrusion sets like REF4578, stealthy macOS evasion campaigns, and novel ransomware tactics directly inform our open detection rules and protection models.
But it doesn’t stop there. Elastic Security is a unified SIEM and XDR solution; so, our continuous investigations also recently included emerging threats like Microsoft Entra ID OAuth Phishing and leveraging Amazon S3’s Server-Side Encryption with Customer-Provided Keys (SSE-C) for ransom/extortion operations in the cloud. This closes the feedback loop between threat discovery and real-time defense, ensuring Elastic’s unified security platform is always evolving in step with adversaries.
Enterprises today operate across Windows, macOS, and Linux endpoints, cloud-native Kubernetes workloads, on-premises servers and laptops, and devices like Microsoft Surface tablets. The edge is everywhere and it is a commodity. What matters is context: unifying all those edges in one platform where data is ingested seamlessly, analytics and AI apply natively, and teams can detect and respond without compromise. With Elastic, customers get exactly that, plus a proven endpoint solution included for free, because effective endpoint protection should be the expectation.
Mike Nichols, VP, Product Management, Elastic Security
Read the excerpt
For more information, read our IDC MarketScape Worldwide XDR 2025 Vendor Assessment excerpt, and start your Elastic Cloud free trial.
IDC MarketScape vendor analysis model is designed to provide an overview of the competitive fitness of technology and suppliers in a given market. The research methodology utilizes a rigorous scoring methodology based on both qualitative and quantitative criteria that results in a single graphical illustration of each supplier’s position within a given market. The Capabilities score measures supplier product, go-to-market and business execution in the short-term. The Strategy score measures alignment of supplier strategies with customer requirements in a 3-5-year timeframe. Supplier market share is represented by the size of the icons.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.