WARNING: Version 6.2 of Elasticsearch has passed its EOL date.
This documentation is no longer being maintained and may be removed. If you are running this version, we strongly advise you to upgrade. For the latest information, see the current release documentation.
After you install Elasticsearch, you can optionally obtain and install X-Pack. For more information about how to obtain X-Pack, see https://www.elastic.co/products/x-pack.
You must run the version of X-Pack that matches the version of Elasticsearch you are running. See the Elastic Support Matrix for more information about product compatibility.
If you are installing X-Pack for the first time on an existing cluster, you must perform a full cluster restart. Installing X-Pack enables security and security must be enabled on ALL nodes in a cluster for the cluster to operate correctly. When upgrading you can usually perform a rolling upgrade.
The following diagram provides an overview of the steps that are required to set up X-Pack on Elasticsearch:
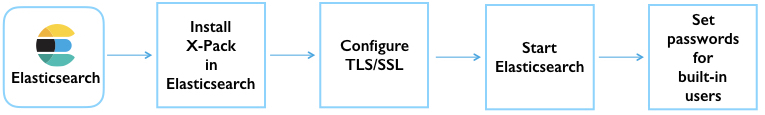
To install X-Pack in Elasticsearch:
-
Optional: If you want to install X-Pack on a machine that doesn’t have internet access:
-
Manually download the X-Pack zip file:
https://artifacts.elastic.co/downloads/packs/x-pack/x-pack-6.2.4.zip(sha512)The plugins for Elasticsearch, Kibana, and Logstash are included in the same zip file. If you have already downloaded this file to install X-Pack on one of those other products, you can reuse the same file.
- Transfer the zip file to a temporary directory on the offline machine. (Do NOT put the file in the Elasticsearch plugins directory.)
-
-
Run
bin/elasticsearch-plugin installfromES_HOMEon each node in your cluster:bin/elasticsearch-plugin install x-pack
If you are using a DEB/RPM distribution of Elasticsearch, run the installation with superuser permissions.
The plugin install scripts require direct internet access to download and install X-Pack. If your server doesn’t have internet access, specify the location of the X-Pack zip file that you downloaded to a temporary directory.
bin/elasticsearch-plugin install file:///path/to/file/x-pack-6.2.4.zip
You must specify an absolute path to the zip file after the
file://protocol. -
Confirm that you want to grant X-Pack additional permissions.
Specify the
--batchoption when running the install command to automatically grant these permissions and bypass these install prompts.-
X-Pack needs these permissions to set the threat context loader during install so Watcher can send email notifications.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: plugin requires additional permissions @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ * java.lang.RuntimePermission accessClassInPackage.com.sun.activation.registries * java.lang.RuntimePermission getClassLoader * java.lang.RuntimePermission setContextClassLoader * java.lang.RuntimePermission setFactory * java.security.SecurityPermission createPolicy.JavaPolicy * java.security.SecurityPermission getPolicy * java.security.SecurityPermission putProviderProperty.BC * java.security.SecurityPermission setPolicy * java.util.PropertyPermission * read,write * java.util.PropertyPermission sun.nio.ch.bugLevel write * javax.net.ssl.SSLPermission setHostnameVerifier See http://docs.oracle.com/javase/8/docs/technotes/guides/security/permissions.html for descriptions of what these permissions allow and the associated risks. Continue with installation? [y/N]y
-
X-Pack requires permissions to enable Elasticsearch to launch the machine learning analytical engine. The native controller ensures that the launched process is a valid machine learning component. Once launched, communications between the machine learning processes and Elasticsearch are limited to the operating system user that Elasticsearch runs as.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: plugin forks a native controller @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ This plugin launches a native controller that is not subject to the Java security manager nor to system call filters. Continue with installation? [y/N]y
-
-
X-Pack will try to automatically create a number of indices within Elasticsearch. By default, Elasticsearch is configured to allow automatic index creation, and no additional steps are required. However, if you have disabled automatic index creation in Elasticsearch, you must configure
action.auto_create_indexinelasticsearch.ymlto allow X-Pack to create the following indices:action.auto_create_index: .security,.monitoring*,.watches,.triggered_watches,.watcher-history*,.ml*
If you are using Logstash or Beats then you will most likely require additional index names in your
action.auto_create_indexsetting, and the exact value will depend on your local configuration. If you are unsure of the correct value for your environment, you may consider setting the value to*which will allow automatic creation of all indices. -
Configure Transport Layer Security (TLS/SSL).
If you have a non-trial license and you want to use X-Pack security, you must configure TLS for internode-communication.
This requirement applies to clusters with more than one node and to clusters with a single node that listens on an external interface. Single-node clusters that use a loopback interface do not have this requirement. For more information, see Encrypting Communications.
-
Start Elasticsearch.
bin/elasticsearch
-
Set the passwords for all built-in users. The
setup-passwordscommand is the simplest method to set the built-in users' passwords for the first time.For example, you can run the command in an "interactive" mode, which prompts you to enter new passwords for the
elastic,kibana, andlogstash_systemusers:bin/x-pack/setup-passwords interactive
For more information about the command options, see setup-passwords.
The
setup-passwordscommand uses a transient bootstrap password that is no longer valid after the command runs successfully. You cannot run thesetup-passwordscommand a second time. Instead, you can update passwords from the Management > Users UI in Kibana or use the security user API.For more information, see Setting Built-in User Passwords.
- Optional: Configure the Java Client.
- Install X-Pack on Kibana.
- Install X-Pack on Logstash.
If you use the DEB/RPM packages to install Elasticsearch, by default Elasticsearch is installed
in /usr/share/elasticsearch and the configuration files are stored
in /etc/elasticsearch. (For the complete list of default paths, see
Debian Directory Layout and
RPM Directory Layout in the Elasticsearch Reference.)
To install X-Pack on a DEB/RPM package installation, you need to run
bin/plugin install from the /usr/share/elasticsearch directory with superuser
permissions:
cd /usr/share/elasticsearch sudo bin/elasticsearch-plugin install x-pack
If the configuration files are not in /etc/elasticsearch you need to
specify the location of the configuration files by setting the environment
variable ES_PATH_CONF via ES_PATH_CONF=<path>.