Elastic Global Threat Report Breakdown: Defense Evasion

When we published the Elastic Global Threat Report in 2022, it included threat trends and correlations from our analysis of telemetry data shared by our users. In addition to telling us about how well features work for them, it also represents our visibility of the threat landscape.
About 34% of the techniques we saw were related to defense evasion, which we believe is a direct result of endpoint security innovations. Because we believe in free and open principles, we wanted to get a little deeper into what we observed and why it’s important for 2023 and beyond.
What’s the defense evasion category?
The Defense Evasion tactic includes 42 techniques at the time of this publication, dozens of sub-techniques, and a nearly infinite number of procedural variations. In simplest terms, each of these capabilities can be used to avoid detection by an analyst or technology.
During 2022, most of the behaviors we observed were in this category, and that’s not surprising given how security controls have improved over the past few years.
A decade ago (when Windows XP was still pretty common in Enterprises), few organizations had a powerful endpoint deployed to detect and mitigate technique-level threat capabilities. If they did, it was prohibitively expensive and needed many hours of manual configuration to get results.
Those days of weak visibility and strictly premium options for shaping the environment are behind us. Powerful tools like Elastic Endpoint are freely available and come equipped with capabilities that quickly mitigate threats. Just as security instrumentation became more sophisticated, so have operating systems. Together with a heightened awareness of threats, these factors mean adversaries need to work faster or buy themselves time by being evasive.
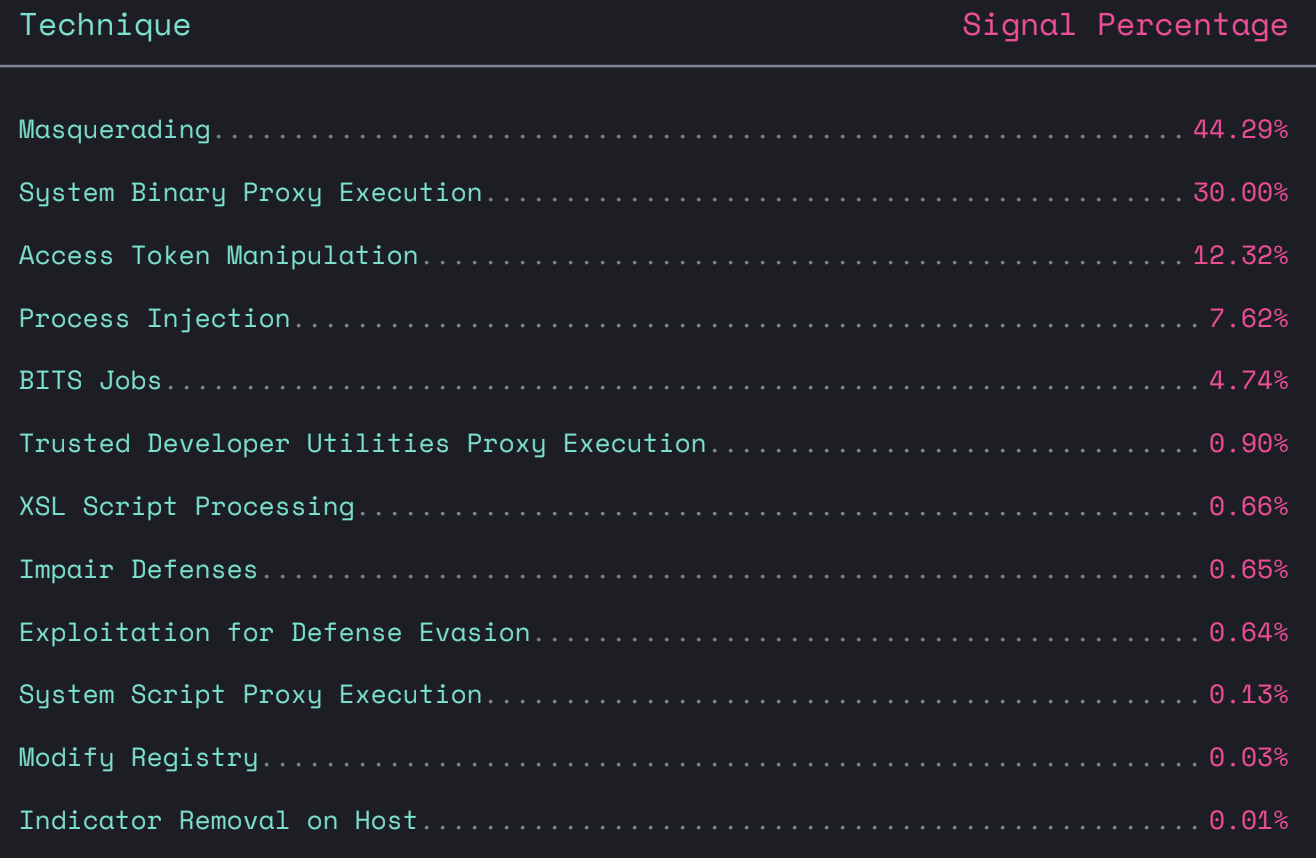
Our Global Threat Report revealed the following breakdown of preferred adversary techniques:
What kinds of defense evasions did we see?
In 2022, we saw more than 15,000 defense evasion attempts using the following techniques (all available to the community via the detection-rules or protections-artifacts repositories in compatible rule formats): MasqueradingSystem Binary Proxy ExecutionAccess Token ManipulationProcess InjectionBITS JobsTrusted Developer Utilities Proxy ExecutionXSL Script ProcessingImpair DefensesExploitation for Defense EvasionSystem Script Proxy ExecutionModify RegistryIndicator Removal on Host
Masquerading does not require an expensive mask
Masquerading and System Binary Proxy Execution were the two most common defense evasion techniques, representing roughly 74% of attempts we observed. This is perhaps unsurprising because these techniques are also simple, free, and effective against some types of immature security technologies.
Masquerading attempts to convince an observer (user or security instrumentation) that something malicious (behavior, capability) is benign/legitimate. An example of masquerading might be executing malware renamed svchost.exe to blend in with other legitimate processes on a system.
Living off the land with built-in proxies
Binary proxy execution is an attempt to execute malicious capabilities using an indirect/secondary mechanism, usually built-in software that is otherwise benign. Common examples include administrative utilities like MSBuild or rundll32, and executing in a privileged context like local administrator may bypass security and other controls.
What are the most effective rules for detection?
Elastic has 48 rules for various defense evasion techniques, and 3 of those rules were responsible for about 45% of events: Binary Masquerading via Untrusted PathParent Process PID SpoofingSuspicious Parent/Child Relationship
For an example of a binary masquerading via an untrusted path, look no further than explorer.exe. The legitimate explorer.exe can be found in c:\windows* where it plays an important role in the UX for Windows operating systems. A malicious binary can be renamed explorer.exe and deployed to other directories, like **C:\windows\debug*, to confuse an analyst or security sensor.
Parent process PID spoofing is just that: a malicious process returns the PID of a trusted process instead of its own, which can elevate privileges through inheritance or defeat parent-child detection mechanisms. If your security instrumentation is looking for unusual processes spawned from outlook.exe, this could change that to practically any other process.
Suspicious parent-child relationship was the next most popular rule in the defense evasion category. Most system processes designed with the operating system in mind execute system software predictably — every time network services are started, they are started in the exact same way. Therefore, a winning detection strategy may be to look for services started atypically, or even rarely. This same concept can be broadly applied to cover several different kinds of defense evasion. One example might be installutil.exe as a descendant of winword.exe, indicating the Word application launched installutil.exe, a utility for installing software. Using the ProblemChild and Living off the Land machine learning integrations can help identify suspicious parent-child relationships.
What next?
Adversaries will continue to abuse built-in binary proxies to evade security instrumentation in 2023. Many benign utilities will dutifully execute malware, which alone may defeat inexperienced human analysts. Some security tools don’t monitor or analyze these second-order executions, allowing an attacker to succeed. Visibility is the first step toward achieving a capability that puts your environment under your control.
Elastic Security provides both. Access our full Elastic Global Threat Report findings to stay up-to-date on the latest adversary trends we’re detecting.

