Microsoft module
editMicrosoft module
editThis is a module for ingesting data from the different Microsoft Products. Currently supports these filesets:
-
defender_atpfileset: Supports Microsoft Defender for Endpoint (Microsoft Defender ATP) -
m365_defenderfileset: Supports Microsoft 365 Defender (Microsoft Threat Protection) -
dhcpfileset: Supports Microsoft DHCP logs
When you run the module, it performs a few tasks under the hood:
- Sets the default paths to the log files (but don’t worry, you can override the defaults)
- Makes sure each multiline log event gets sent as a single event
- Uses an Elasticsearch ingest pipeline to parse and process the log lines, shaping the data into a structure suitable for visualizing in Kibana
- Deploys dashboards for visualizing the log data
Read the quick start to learn how to configure and run modules.
Configure the module
editYou can further refine the behavior of the microsoft module by specifying
variable settings in the
modules.d/microsoft.yml file, or overriding settings at the command line.
You must enable at least one fileset in the module. Filesets are disabled by default.
Variable settings
editEach fileset has separate variable settings for configuring the behavior of the
module. If you don’t specify variable settings, the microsoft module uses
the defaults.
For advanced use cases, you can also override input settings. See Override input settings.
When you specify a setting at the command line, remember to prefix the
setting with the module name, for example, microsoft.defender_atp.var.paths
instead of defender_atp.var.paths.
m365_defender fileset settings
editTo configure access for Filebeat to Microsoft 365 Defender you will have to create a new Azure Application registration, this will again return Oauth tokens with access to the Microsoft 365 Defender API
The procedure to create an application is found on the below link:
Create a new Azure Application
When giving the application the API permissions described in the documentation (Incident.Read.All) it will only grant access to read Incidents from 365 Defender and nothing else in the Azure Domain.
After the application has been created, it should contain 3 values that you need to apply to the module configuration.
These values are:
- Client ID
- Client Secret
- Tenant ID
Example config:
- module: microsoft
m365_defender:
enabled: true
var.oauth2.client.id: "123abc-879546asd-349587-ad64508"
var.oauth2.client.secret: "980453~-Sg99gedf"
var.oauth2.token_url: "https://login.microsoftonline.com/INSERT-TENANT-ID/oauth2/v2.0/token"
var.oauth2.scopes:
- "https://api.security.microsoft.com/.default"
-
var.oauth2.client.id - This is the client ID related to creating a new application on Azure.
-
var.oauth2.client.secret - The secret related to the client ID.
-
var.oauth2.token_url - A predefined URL towards the Oauth2 service for Microsoft. The URL should always be the same with the exception of the Tenant ID that needs to be added to the full URL.
-
var.oauth2.scopes - A list of included scopes, should use .default unless different is specified.
365 Defender ECS fields
editThis is a list of 365 Defender fields that are mapped to ECS.
| 365 Defender Fields | ECS Fields | |
|---|---|---|
lastUpdateTime |
@timestamp |
|
severity |
event.severity |
|
createdTime |
event.created |
|
alerts.category |
threat.technique.name |
|
alerts.description |
rule.description |
|
alerts.serviceSource |
event.provider |
|
alerts.alertId |
event.id |
|
alerts.firstActivity |
event.start |
|
alerts.lastActivity |
event.end |
|
alerts.title |
message |
|
entities.processId |
process.pid |
|
entities.processCommandLine |
process.command_line |
|
entities.processCreationTime |
process.start |
|
entities.parentProcessId |
process.parent.pid |
|
entities.parentProcessCreationTime |
process.parent.start |
|
entities.sha1 |
file.hash.sha1 |
|
entities.sha256 |
file.hash.sha256 |
|
entities.url |
url.full |
|
entities.filePath |
file.path |
|
entities.fileName |
file.name |
|
entities.userPrincipalName |
host.user.name |
|
entities.domainName |
host.user.domain |
|
entities.aadUserId |
host.user.id |
defender_atp fileset settings
editTo allow the filebeat module to ingest data from the Microsoft Defender API, you would need to create a new application on your Azure domain.
The procedure to create an application is found on the below link:
Create a new Azure Application
When giving the application the API permissions described in the documentation (Windows Defender ATP Alert.Read.All) it will only grant access to read alerts from ATP and nothing else in the Azure Domain.
After the application has been created, it should contain 3 values that you need to apply to the module configuration.
These values are:
- Client ID
- Client Secret
- Tenant ID
Example config:
- module: microsoft
defender_atp:
enabled: true
var.oauth2.client.id: "123abc-879546asd-349587-ad64508"
var.oauth2.client.secret: "980453~-Sg99gedf"
var.oauth2.token_url: "https://login.microsoftonline.com/INSERT-TENANT-ID/oauth2/token"
-
var.oauth2.client.id - This is the client ID related to creating a new application on Azure.
-
var.oauth2.client.secret - The secret related to the client ID.
-
var.oauth2.token_url - A predefined URL towards the Oauth2 service for Microsoft. The URL should always be the same with the exception of the Tenant ID that needs to be added to the full URL.
Defender ATP ECS fields
editThis is a list of Defender ATP fields that are mapped to ECS.
| Defender ATP Fields | ECS Fields | |
|---|---|---|
alertCreationTime |
@timestamp |
|
aadTenantId |
cloud.account.id |
|
category |
threat.technique.name |
|
computerDnsName |
host.hostname |
|
description |
rule.description |
|
detectionSource |
observer.name |
|
evidence.fileName |
file.name |
|
evidence.filePath |
file.path |
|
evidence.processId |
process.pid |
|
evidence.processCommandLine |
process.command_line |
|
evidence.processCreationTime |
process.start |
|
evidence.parentProcessId |
process.parent.pid |
|
evidence.parentProcessCreationTime |
process.parent.start |
|
evidence.sha1 |
file.hash.sha1 |
|
evidence.sha256 |
file.hash.sha256 |
|
evidence.url |
url.full |
|
firstEventTime |
event.start |
|
id |
event.id |
|
lastEventTime |
event.end |
|
machineId |
cloud.instance.id |
|
relatedUser.userName |
host.user.name |
|
relatedUser.domainName |
host.user.domain |
|
title |
message |
|
severity |
event.severity |
Dashboards
editThis module comes with a sample dashboard for Defender ATP.
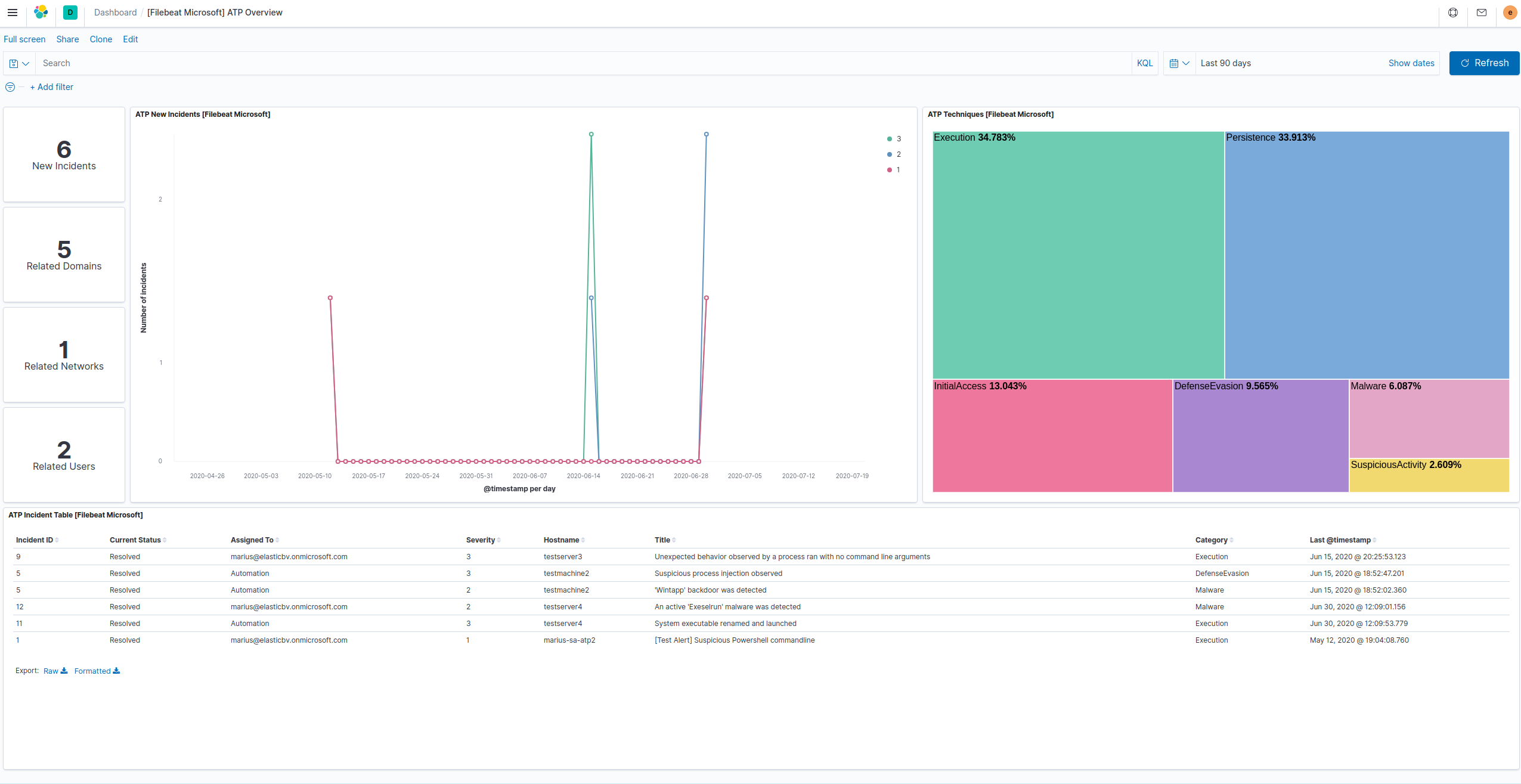
The best way to view Defender ATP events and alert data is in the SIEM.
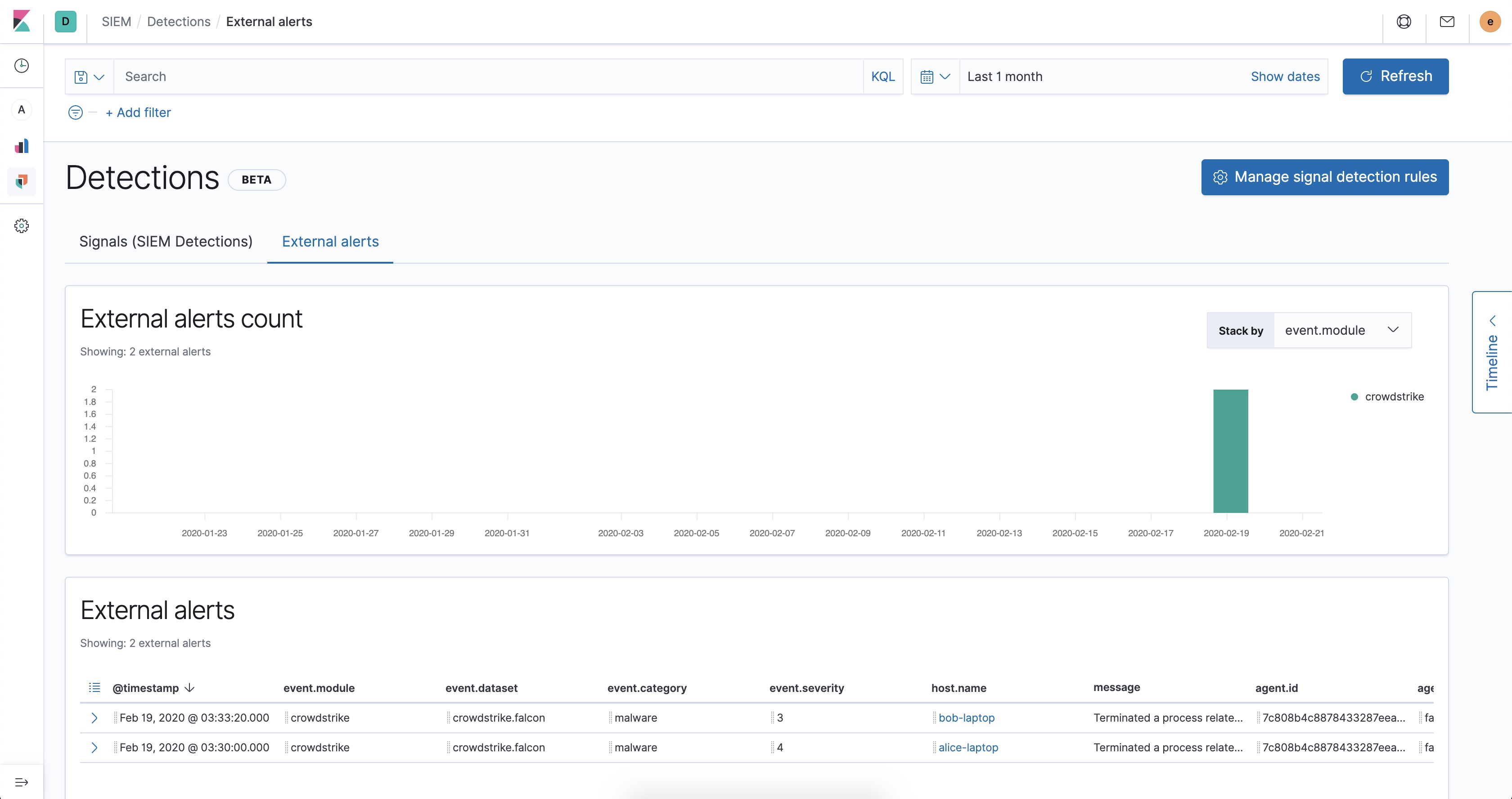
For alerts, go to Detections → External alerts.
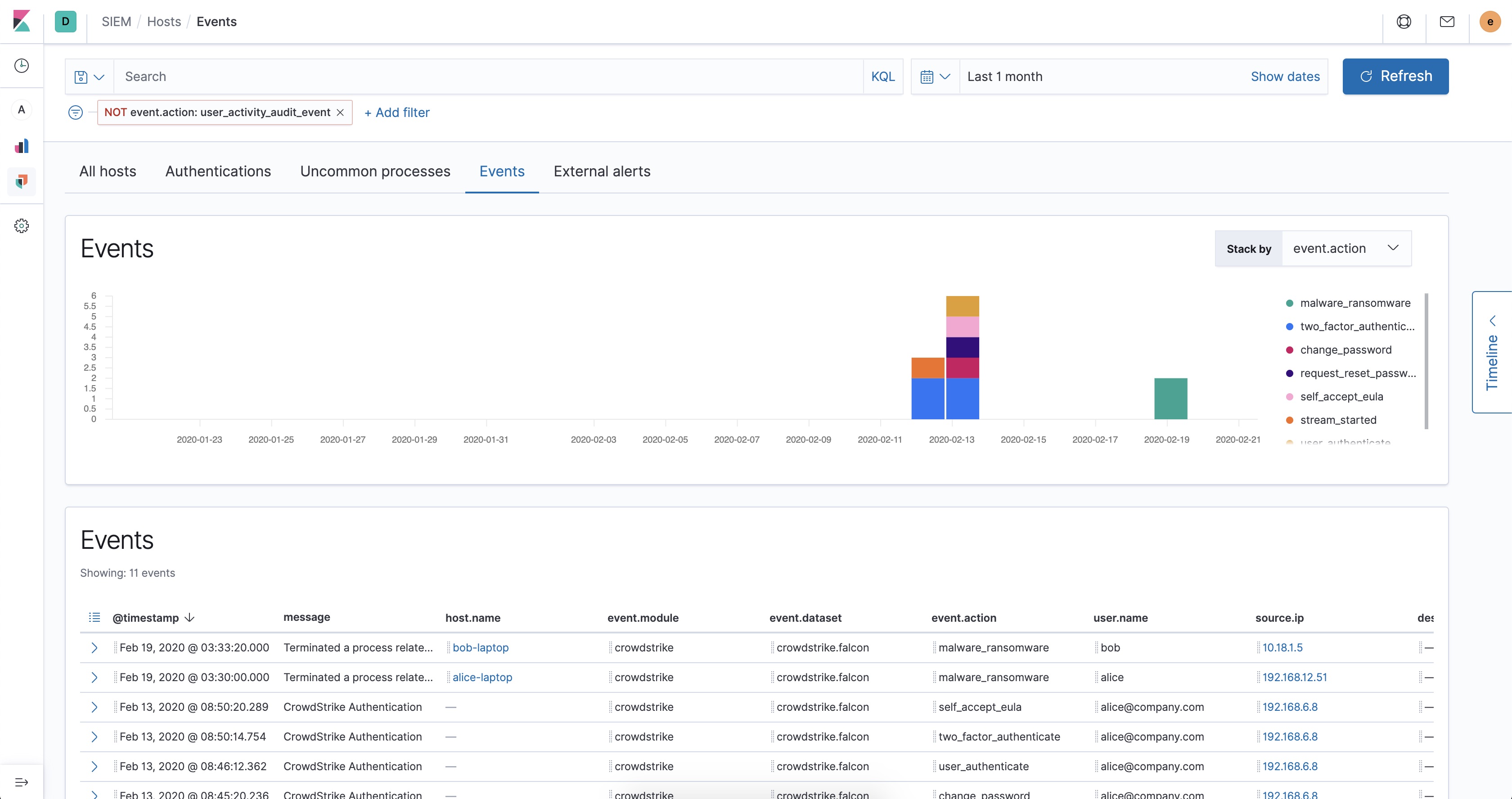
And for all other Defender ATP event types, go to Host → Events.
dhcp fileset settings
editThis functionality is in technical preview and may be changed or removed in a future release. Elastic will work to fix any issues, but features in technical preview are not subject to the support SLA of official GA features.
This was converted from RSA NetWitness log parser XML "msdhcp" device revision 99.
-
var.paths -
An array of glob-based paths that specify where to look for the log files. All
patterns supported by Go Glob
are also supported here. For example, you can use wildcards to fetch all files
from a predefined level of subdirectories:
/path/to/log/*/*.log. This fetches all.logfiles from the subfolders of/path/to/log. It does not fetch log files from the/path/to/logfolder itself. If this setting is left empty, Filebeat will choose log paths based on your operating system. -
var.input -
The input from which messages are read. One of
file,tcporudp. Defaults toudp. -
var.syslog_host -
The address to listen to UDP or TCP based syslog traffic.
Defaults to
localhost. Set to0.0.0.0to bind to all available interfaces. -
var.syslog_port -
The port to listen for syslog traffic. Defaults to
9515
Ports below 1024 require Filebeat to run as root.
-
var.tz_offset -
By default, datetimes in the logs will be interpreted as relative to
the timezone configured in the host where Filebeat is running. If ingesting
logs from a host on a different timezone, use this field to set the timezone
offset so that datetimes are correctly parsed. Valid values are in the form
±HH:mm, for example,
-07:00forUTC-7. -
var.rsa_fields -
Flag to control the addition of non-ECS fields to the event. Defaults to true,
which causes both ECS and custom fields under
rsato be added. -
var.keep_raw_fields -
Flag to control the addition of the raw parser fields to the event. This fields
will be found under
rsa.raw. The default is false.
Fields
editFor a description of each field in the module, see the exported fields section.