Interactive investigation guides
editInteractive investigation guides
editDetection rule investigation guides suggest steps for triaging, analyzing, and responding to potential security issues. For custom rules, you can create an interactive investigation guide that includes buttons for launching runtime queries in Timeline, using alert data and hard-coded literal values. This allows you to start detailed Timeline investigations directly from an alert using relevant data.
Interactive investigation guides are compatible between Elastic Stack versions 8.7.0 and later. Query buttons created in 8.6.x use different syntax and won’t render correctly in later versions, and vice versa.
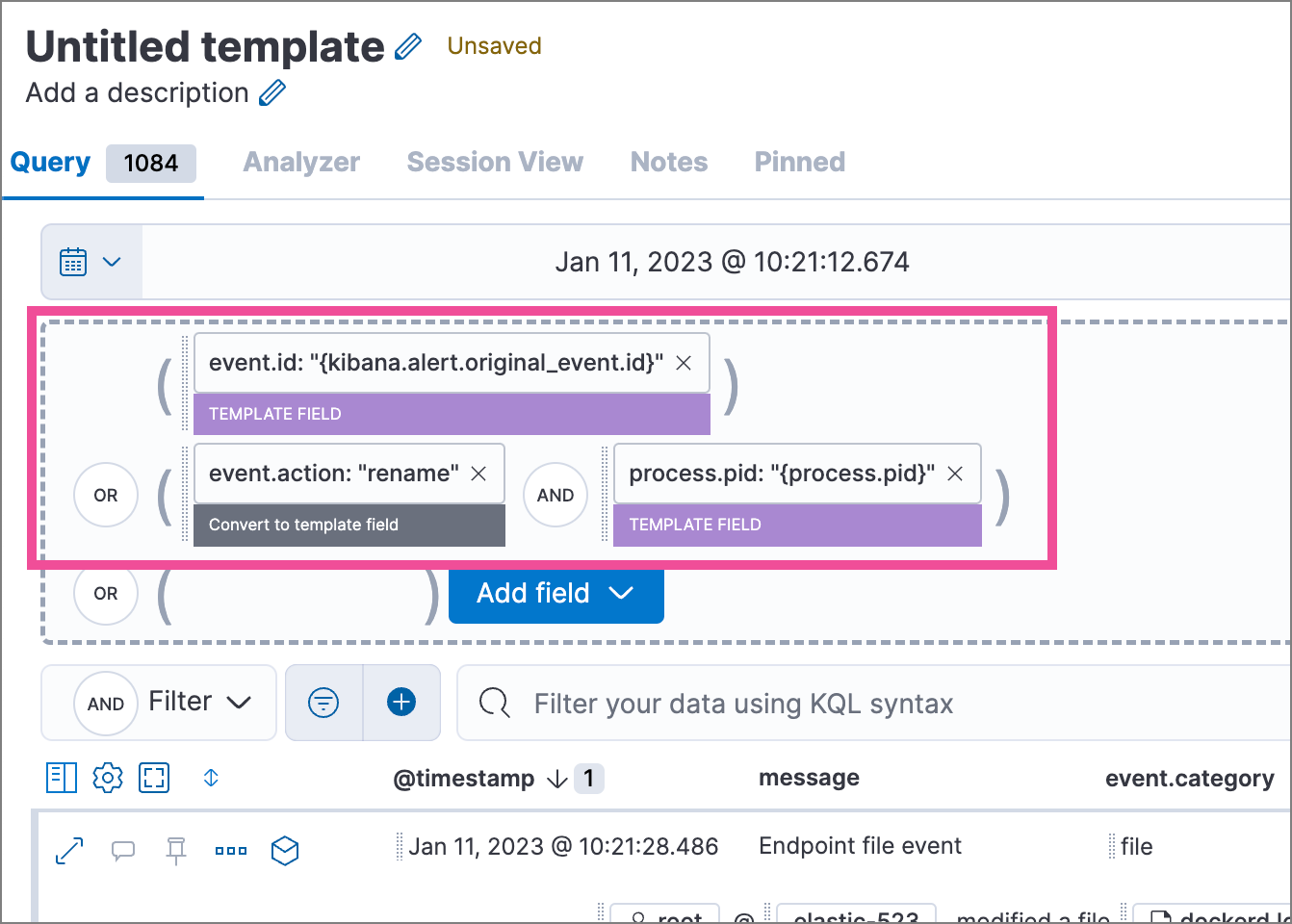
Each query button displays in parentheses the number of documents found. Click the button to automatically create the query in Timeline based on settings specified in the investigation guide.
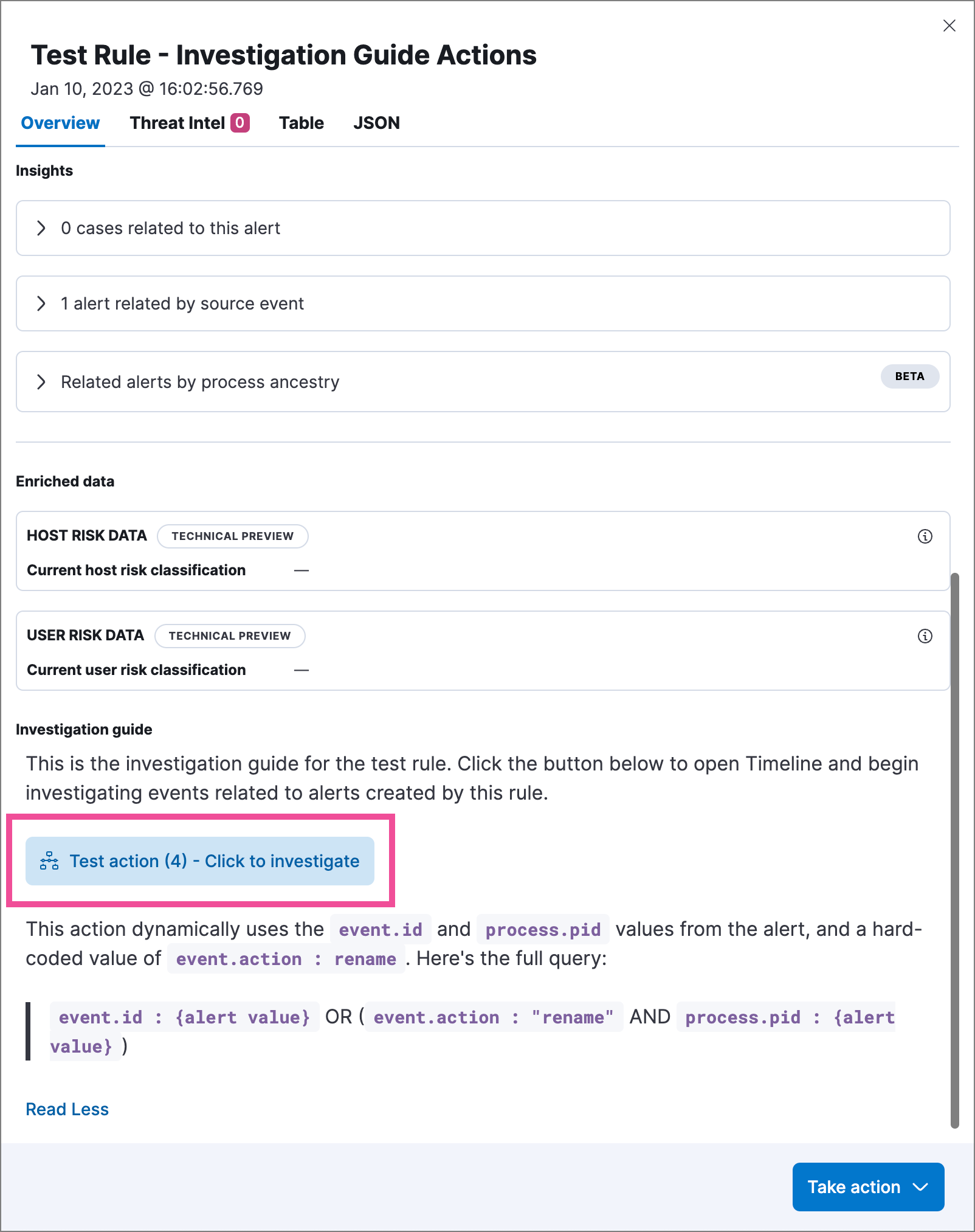
Add investigation guide actions to a rule
editYou can only create interactive investigation guides with custom rules because Elastic prebuilt rules can’t be edited. However, you can duplicate a prebuilt rule, then configure the investigation guide for the duplicated rule.
You can configure an interactive investigation guide when you create a new rule or edit an existing rule. When configuring the rule’s settings (the About rule step for a new rule, or the About tab for an existing rule), expand the Advanced settings, then scroll down to the Investigation guide field.
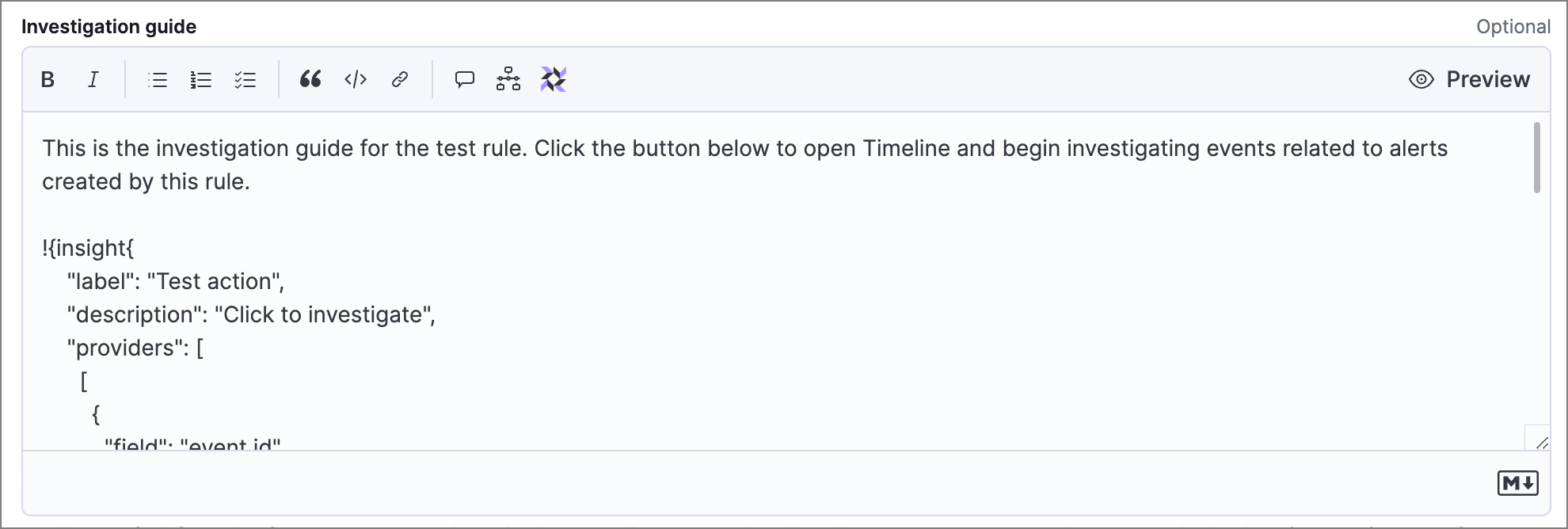
Add the following syntax to the Investigation guide Markdown editor to configure a query. The syntax will appear as a clickable button in the investigation guide.
| Field | Description |
|---|---|
|
The container object holding all the configuration attributes for the button and the query. |
|
Text to identify the button. |
|
Additional text to include on the button. |
|
A two-level nested array that defines the query you want to run in Timeline. Similar to the structure of queries in Timeline, items in the outer level are joined by an Each item in
|
Some characters must be escaped with a backslash, such as \" for a quotation mark and \\ for a literal backslash. Windows paths must be divided with double backslashes (for example, C:\\Windows\\explorer.exe), and paths that already include double backslashes might require four backslashes for each divider. A clickable error icon (![]() ) displays below the Markdown editor if there are any syntax errors.
) displays below the Markdown editor if there are any syntax errors.
Example syntax
edit!{insight{
"label": "Test action",
"description": "Click to investigate",
"providers": [
[
{"field": "event.id", "value": "kibana.alert.original_event.id", "type": "parameter"}
],
[
{"field": "event.action", "value": "rename", "type": "literal"},
{"field": "process.pid", "value": "process.pid", "type": "parameter"}
]
]
}}
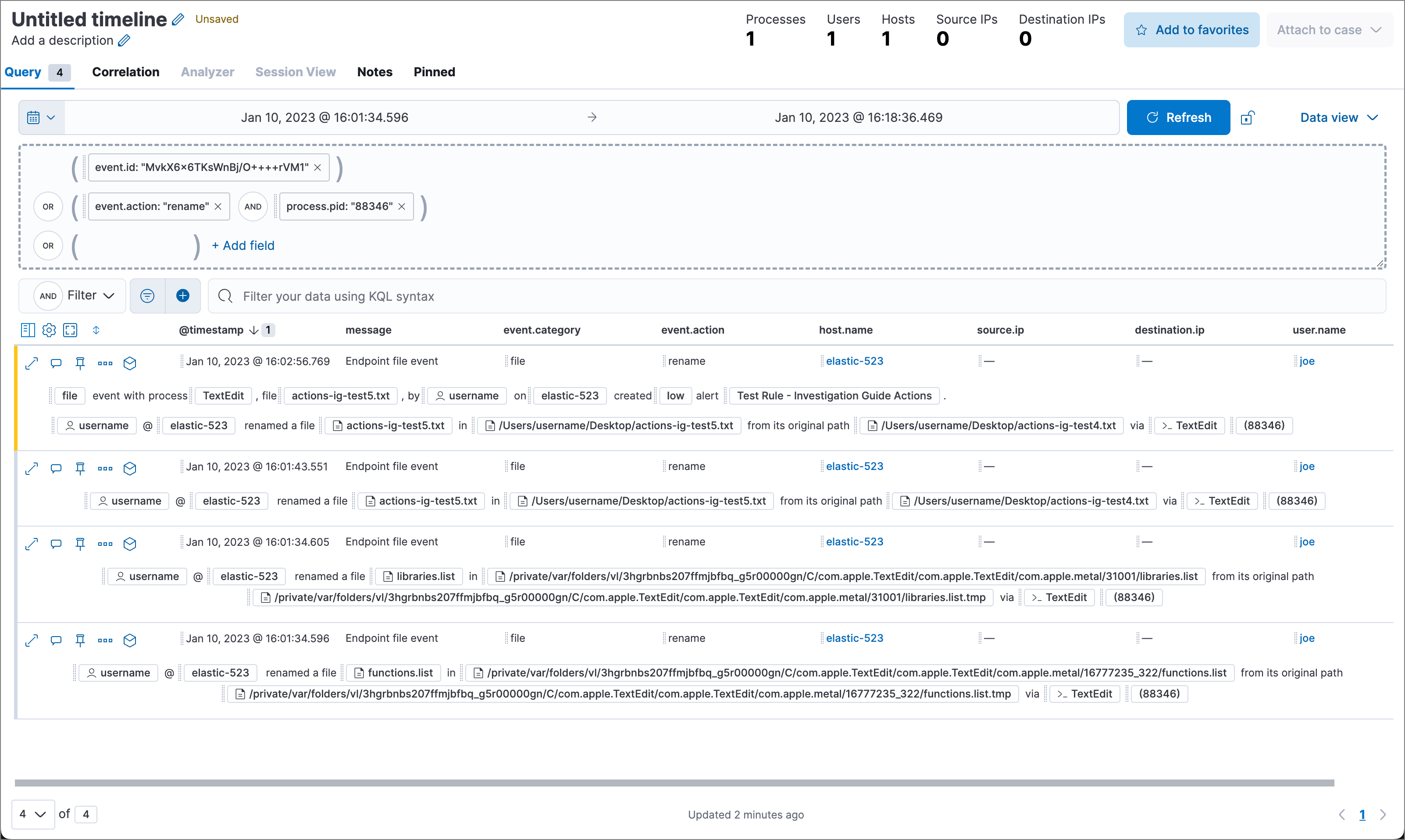
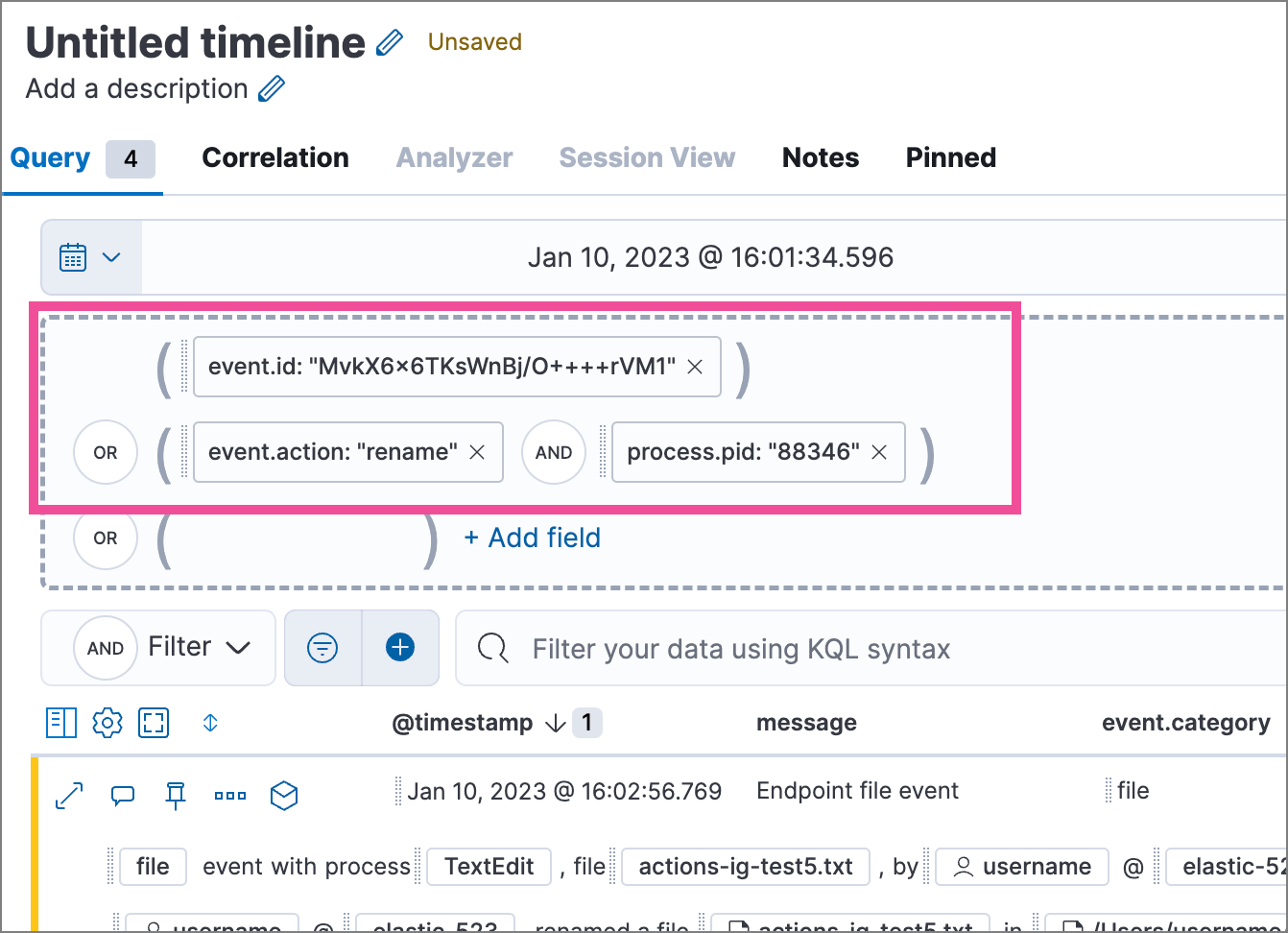
This example creates the following Timeline query, as illustrated below:
(event.id : <alert value>)
OR (event.action : "rename" AND process.pid : <alert value>)
Timeline template fields
editWhen viewing an interactive investigation guide in contexts unconnected to a specific alert (such a rule’s details page), queries open as Timeline templates, and parameter fields are treated as Timeline template fields.