Benchmark rules
editBenchmark rules
editThe Benchmark Integrations page lets you view the cloud security posture (CSP) benchmark rules for the Kubernetes security posture management (KSPM) integration.
Benchmark rules are used by the KSPM integration to identify configuration risks in Kubernetes. Benchmark rules are based on the Center for Internet Security’s (CIS) secure configuration benchmarks for Kubernetes.
Each benchmark rule checks to see if a specific Kubernetes resource is configured according to a CIS Benchmark. The names of rules describe what they check, for example:
-
Ensure Kubernetes Secrets are encrypted using Customer Master Keys (CMKs) managed in AWS KMS -
Ensure the default namespace is not in use
When benchmark rules are evaluated, the resulting findings data appears on the Cloud Posture dashboard.
To find the Benchmark Integrations page, go to Manage → CSP Benchmarks. From there, you can view the benchmark rules associated with an existing integration by clicking the integration name.
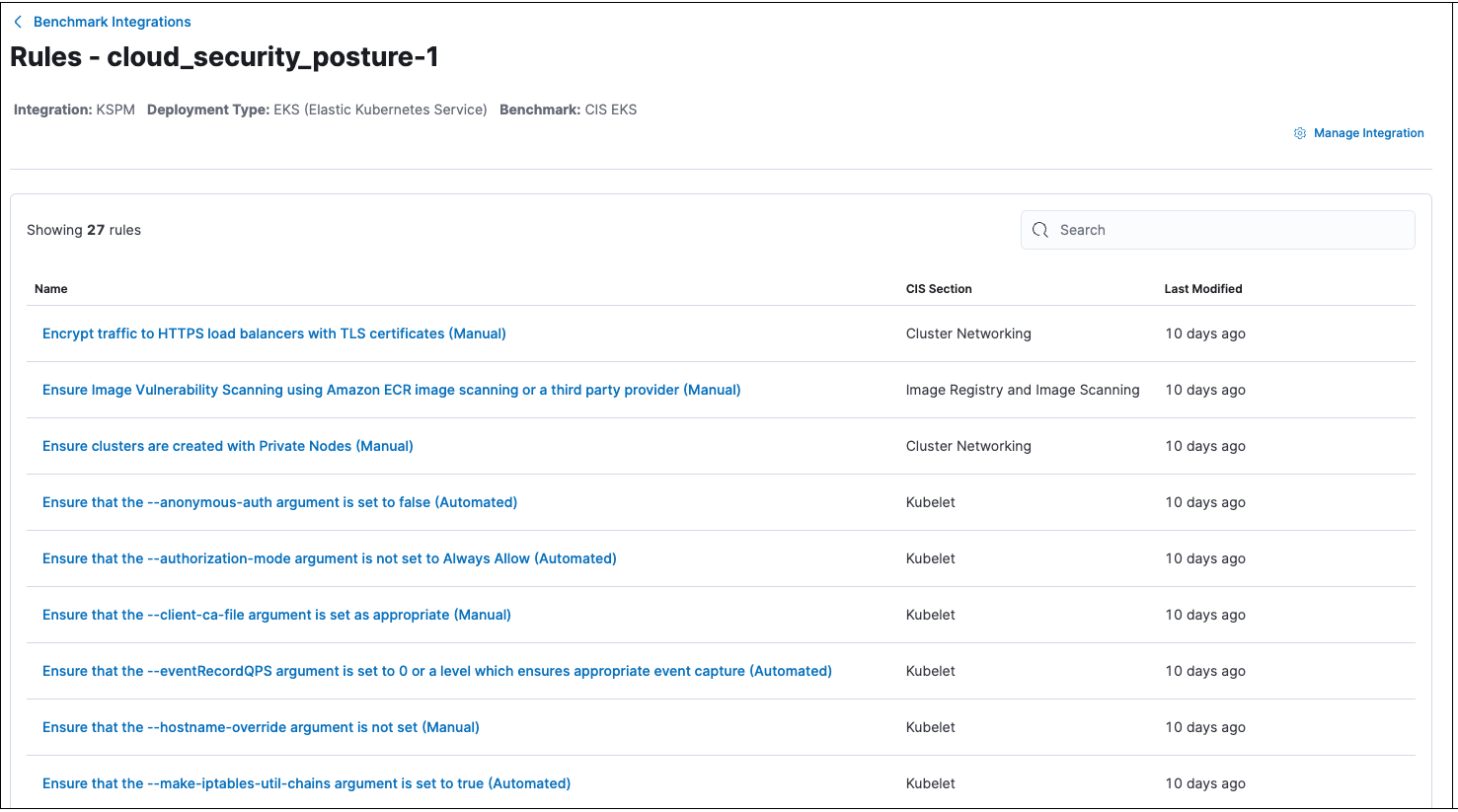
You can then click on a benchmark rule’s name to see details, including information about how to remediate failures and related links.
Benchmark rules are not editable.
How benchmark rules work
edit- When a KSPM integration is deployed, and every four hours after that, Elastic Agent fetches relevant Kubernetes resources.
- After Kubernetes resources are fetched, they are evaluated against all applicable benchmark rules.
-
Finding values of
passorfailindicate whether the standards defined by benchmark rules were met.