Configure advanced settings
editConfigure advanced settings
editThe advanced settings determine:
- Which indices Elastic Security uses to retrieve data
- Whether the news feed is displayed on the Overview page
- The default time interval used to filter Elastic Security pages
- The default Elastic Security pages refresh time
- Machine learning anomaly score display threshold
- Which IP reputation links appear on IP detail pages
You need All privileges for the Advanced Settings feature to change these
settings (see Kibana privileges).
Modifying advanced settings can affect Kibana performance and cause problems that are difficult to diagnose. Setting a property value to a blank field reverts to the default behavior, which might not be compatible with other configuration settings. Deleting a custom setting removes it from Kibana permanently.
Access advanced settings
editTo access advanced settings:
- Go to Stack Management > Advanced Settings.
-
Scroll down to Security Solution settings.
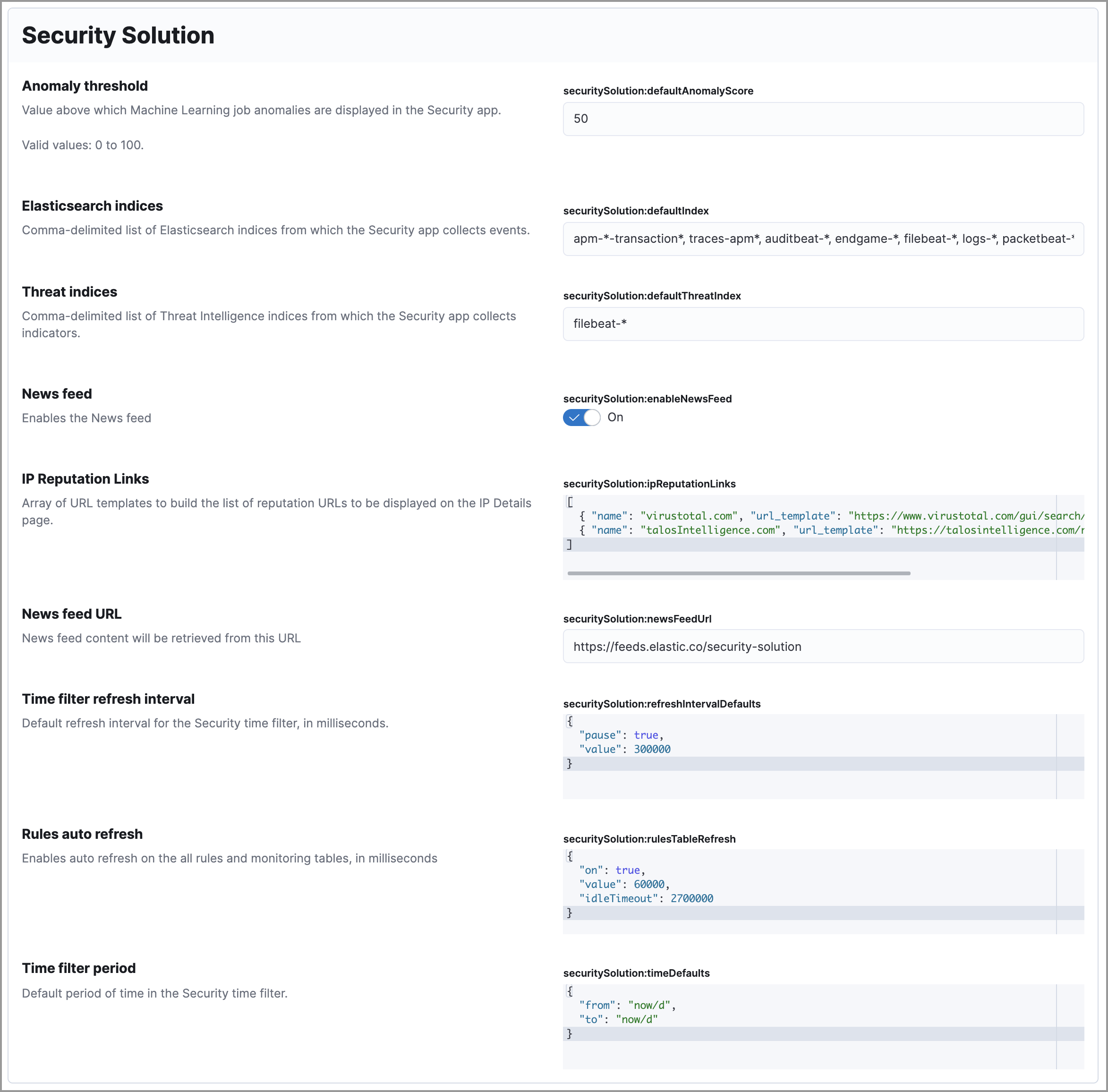
Update default Elastic Security indices
editThe securitySolution:defaultIndex field defines which Elasticsearch indices the
Elastic Security app uses to collects data. By default, these index patterns are used to
match Elasticsearch indices:
-
apm-*-transaction* -
auditbeat-* -
endgame-* -
filebeat-* -
logs-* -
packetbeat-* -
winlogbeat-*
Index patterns use wildcards to specify a set of indices. For example, the
filebeat-* index pattern means all indices starting with filebeat- are
available in the Elastic Security app.
All of the default index patterns match Beats and Elastic Agent indices. This means all data shipped via Beats and the Elastic Agent is automatically added to the Elastic Security app.
You can add or remove any indices and index patterns as required. For some background information on Elasticsearch indices, see Data in: documents and indices.
If you leave the logs-* index selected, by default, all Elastic cloud logs are excluded from all queries in the Elastic Security app. This is to avoid adding data from cloud monitoring to the app.
Elastic Security requires ECS-compliant data. If you use third-party data collectors to ship data to Elasticsearch, the data must be mapped to ECS. Elastic Security ECS field reference lists ECS fields used in Elastic Security.
Update default Elastic Security threat intelligence indices
editThe securitySolution:defaultThreatIndex advanced setting defines threat intelligence indices that Elastic Security will use when collecting threat indicators. The setting controls features that query threat indices, such as the Threat Intelligence view on the Overview page and threat indicator match rules. One or more threat intelligence indices can be defined; the filebeat-* index is specified by default.
Threat intelligence indices aren’t required to be ECS compatible when used in an indicator match rule. However, we recommend compatibility if you’d like for your alerts to be enriched with relevant threat indicator information. By default, indicator match rules are configured to ingest indicators from the Threat Intel Filebeat module and to check for fields prefixed with threatintel.indicator. See Threat Intel module for more information about these fields. This rule setting is stored in the Indicator prefix override field, under indicator match rule advanced settings. If your indicator data contains indicator fields at a different location, update this field accordingly to ensure alert enrichment can still be performed.
Modify news feed settings
editYou can change these settings, which affect the news feed displayed on the Elastic Security Overview page:
-
securitySolution:enableNewsFeed: Enables the security news feed on the Security Overview page. -
securitySolution:newsFeedUrl: The URL from which the security news feed content is retrieved.
Change the default search interval and data refresh time
editThese settings determine the default time interval and refresh rate Elastic Security pages use to display data when you open the app:
-
securitySolution:timeDefaults: Default time interval -
securitySolution:refreshIntervalDefaults: Default refresh rate
See Date Math for information about the syntax. The UI time filter overrides the default values.
Set machine learning score threshold
editWhen security machine learning jobs are enabled, this setting determines the threshold above which anomaly scores are displayed in Elastic Security:
-
securitySolution:defaultAnomalyScore
Display reputation links on IP detail pages
editOn IP details pages (Security → Network → IP address), links to external sites for verifying the IP address’s reputation are displayed. By default, links to these sites are listed: TALOS and VIRUSTOTAL.
The securitySolution:ipReputationLinks field determines which IP reputation
sites are listed. To modify the listed sites, edit the field’s JSON array. These
fields must be defined in each array element:
-
name: The link’s UI display name. -
url_template: The link’s URL. It can include{{ip}}, which is placeholder for the IP address you are viewing on the IP detail page.
Example
Adds a link to https://www.dnschecker.org on IP detail pages:
[
{ "name": "virustotal.com", "url_template": "https://www.virustotal.com/gui/search/{{ip}}" },
{ "name": "dnschecker.org", "url_template": "https://www.dnschecker.org/ip-location.php?ip={{ip}}" },
{ "name": "talosIntelligence.com", "url_template": "https://talosintelligence.com/reputation_center/lookup?search={{ip}}" }
]