Setup role
editSetup role
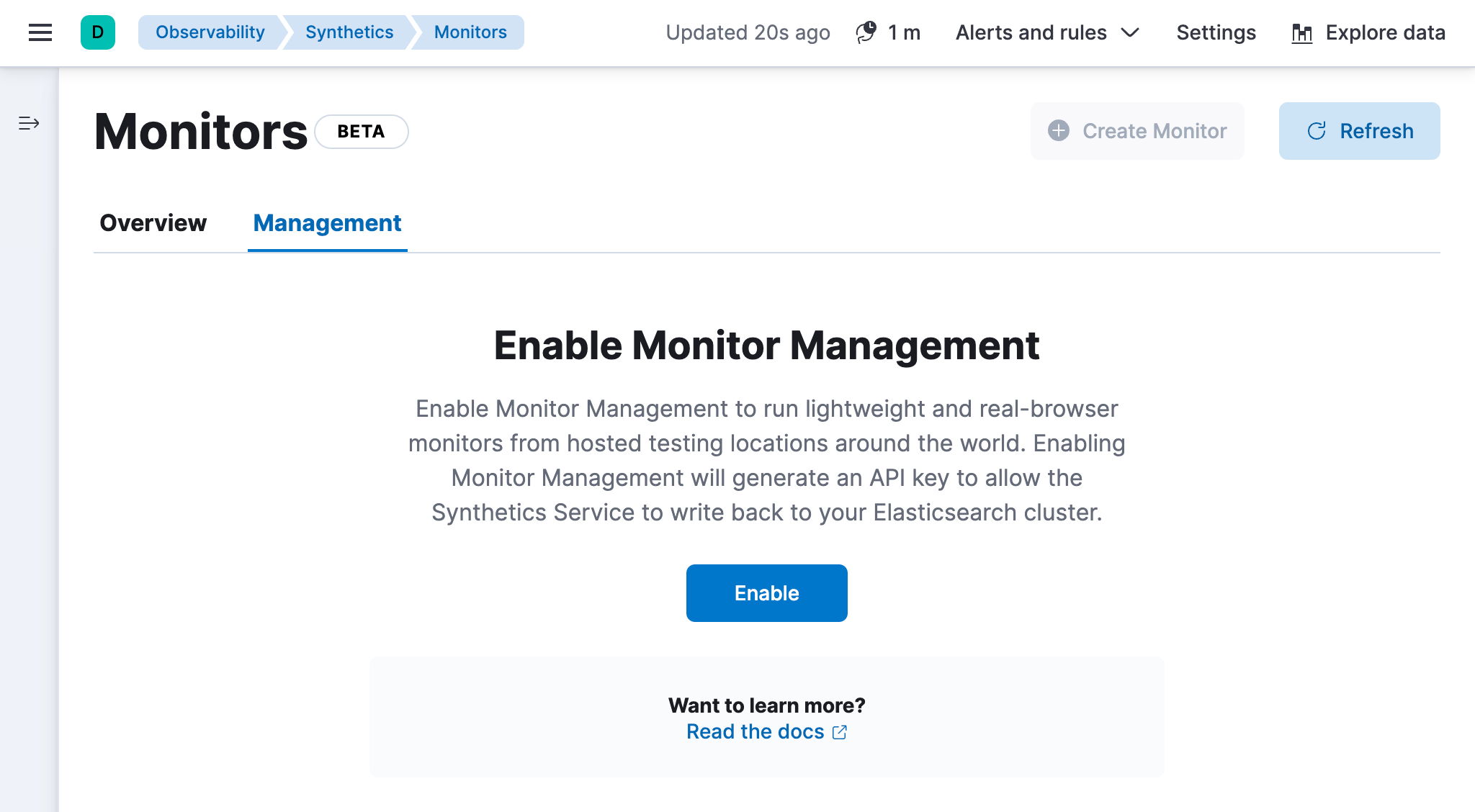
editAdministrators who set up Synthetics typically need to enable Monitor Management.
Enabling Monitor Management is an admin-level task that requires extra privileges and must be completed just once by an admin before any users with the Writer role can create synthetic monitors. This applies to monitors created via both projects and the UI.
As a best practice, grant the setup role to administrators only, and use a more restrictive role for event publishing.
Create a setup role, called something like synthetics_setup:
-
Start with the
editorbuilt-in role. This role grants full access to all features in Kibana (including the Observability solution) and read-only access to data indices.The
editorbuilt-in role will grant write access to all Kibana apps. If you want to limit write access to the Synthetics app only, refer to Limited write access.If you choose this approach, you will still need to grant the privileges in the next step.
-
Grant the role additional privileges that are required to enable Monitor Management:
-
Grant all of the following privileges:
Type Privilege Purpose monitorAllows the user to retrieve cluster details.
read_ilmAllows the user access to all read-only index lifecycle management operations.
read_pipelineGives the user read-only access to the ingest pipline.
synthetics-*:view_index_metadataGives the user read-only access to index and data stream metadata.
synthetics-*:create_docAllows the user to index documents.
synthetics-*:auto_configurePermits auto-creation of indices and data streams.
-
Grant at least one of following privileges:
-