Configure Kibana reporting
Kibana's reporting functionality offers multiple ways to share Discover sessions, dashboards, Visualize Library visualizations, and Canvas workpads.
This section covers the necessary configuration to ensure reporting works correctly in your deployment. For guidance on using reporting features effectively, refer to Reporting and sharing.
Kibana PNG/PDF reporting uses a custom binary of headless Chromium, and support comes with special caveats:
- The functionality requires special OS dependencies which may not be available for all distributions and configurations of Linux.
- It is subject to system resource configurations such as the limited number of file descriptors, allowed processes, and types of processes.
- Linux versions that are in end-of-life phase are not supported.
- Linux systems with
SELinuxorfapolicydare not supported.
Before upgrading Kibana in a production environment, we encourage you to test your screenshotting use cases in a pre-production environment to make sure your hosts support our latest build of Chromium. For the most reliable configuration of PDF/PNG reporting features, consider installing Kibana using Docker, or using Elastic Cloud.
To secure reporting features, you must grant users access to reporting functionality and protect the reporting endpoints with TLS/SSL encryption. Additionally, you can install graphical packages on the operating system to enable screenshot capabilities in the Kibana server.
Report generation requests are authenticated by API keys instead of session cookies. There are several key differences between the authentication methods. API keys capture your role privileges, whereas session cookie are based on your user credentials. API keys are also longer-lived, compared to session cookies, which have a shorter lifespan.
If you have a cross-cluster search environment and want to generate reports from remote clusters, you must have the appropriate cluster and index privileges on the remote cluster and local cluster. For example, if requests are authenticated with an API key, the API key requires certain privileges on the local cluster that contains the local index, in addition to the remote. For more information and examples, refer to Configure roles and users for remote clusters.
Configuring reporting in your environment involves two main areas:
Depending on your license, the type of users, and whether you prefer using the Kibana UI or API, there are multiple ways to grant access to reporting functionality.
The following configurations are required at Elasticsearch, Kibana, and OS levels to support reporting features.
These steps apply only to self-managed deployments. Orchestrated deployments include this configuration by default. For more details on different deployment options, refer to Deploy.
- Secure the reporting endpoints
- Install the dependencies for the headless browser
- Set the
server.hostfor the headless browser - Ensure Elasticsearch allows built-in templates
Choose the method that best fits your use case.
When security is enabled, you grant users access to reporting features with Kibana application privileges, which allow you to create custom roles that control the spaces and applications where users generate reports.
Create the reporting role.
- Go to the Roles management page using the navigation menu or the global search field.
- Click Create role.
Specify the role settings.
Enter the Role name. For example,
custom_reporting_user.Specify the Indices and Privileges.
Access to data is an index-level privilege. For each index that contains the data you want to include in reports, add a line, then give each index
readandview_index_metadataprivileges.NoteIf you use index aliases, you must also grant
readandview_index_metadataprivileges to underlying indices to generate CSV reports.For more information, refer to Security privileges.
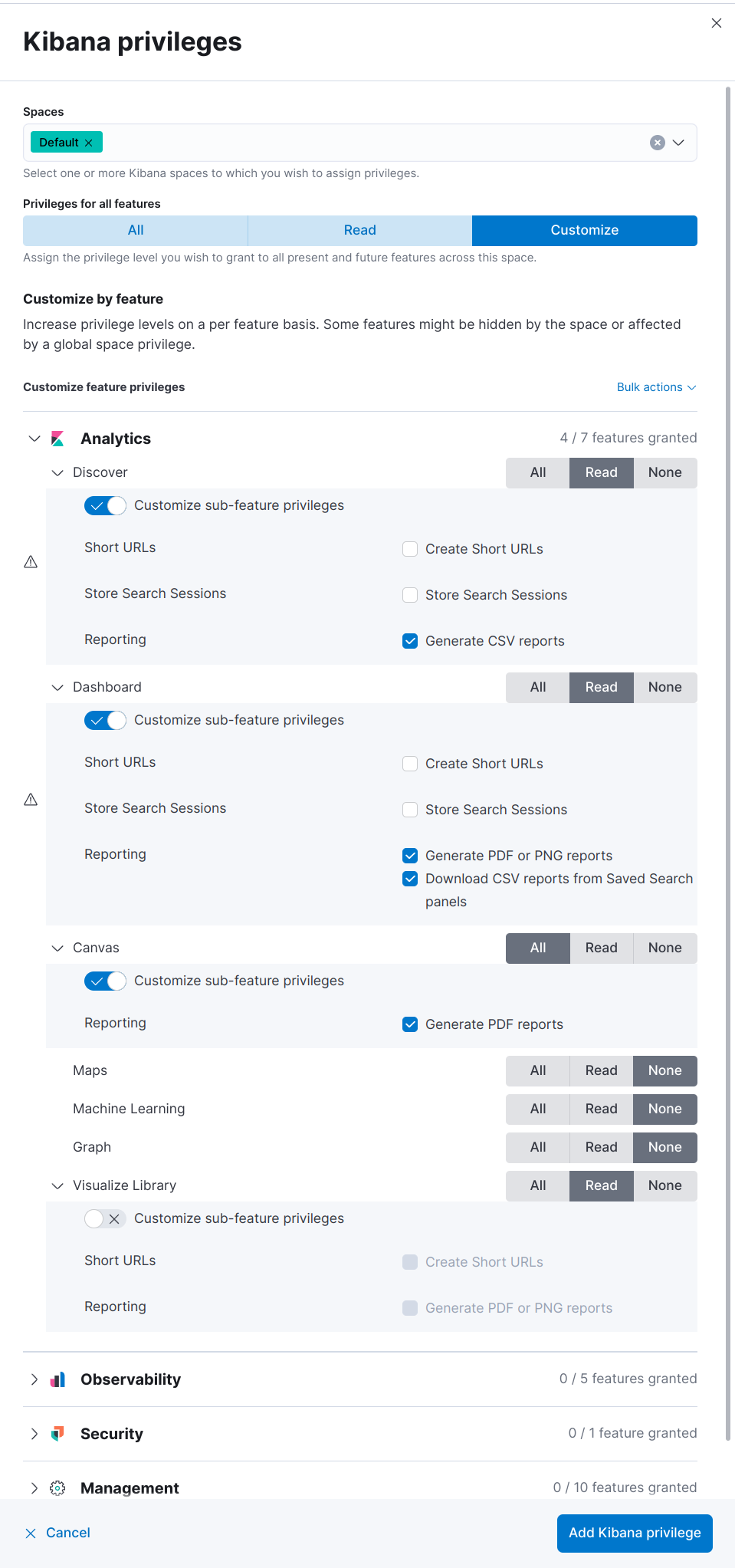
Add the Kibana privileges.
Click Add Kibana privilege.
Select one or more Spaces.
Click Customize, then click Analytics.
For each application, select All, or to customize the privileges, select Read and Customize sub-feature privileges.
NoteIf you have a Basic license, sub-feature privileges are unavailable.
NoteIf the Reporting options for application features are unavailable, and the cluster license is higher than Basic, contact your administrator.
5. Click Add Kibana privilege.
Click Create role.
Assign the reporting role to a user.
- Go to the Users management page using the navigation menu or the global search field.
- Select the user you want to assign the reporting role to.
- From the Roles dropdown, select custom_reporting_user.
- Click Update user.
Granting the privilege to generate reports also grants the user the privilege to view their reports in Reporting. Users can only access their own reports.
To view reports, go to the Reporting management page in the navigation menu or use the global search field.
With Kibana application privileges, you can use the role APIs to grant access to the reporting features, using All privileges, or sub-feature privileges.
This API request needs to be run against the Kibana API endpoint.
PUT <kibana host>:<port>/api/security/role/custom_reporting_user
{
"elasticsearch": {
"cluster": [],
"indices": [],
"run_as": []
},
"kibana": [{
"spaces": ["*"],
"base": [],
"feature": {
"dashboard_v2": ["generate_report",
"download_csv_report"],
"discover_v2": ["generate_report"],
"canvas": ["generate_report"],
"visualize_v2": ["generate_report"]
}
}]
}
- Grants access to generate PNG and PDF reports in Dashboard.
- Grants access to generate CSV reports from saved Discover session panels in Dashboard.
- Grants access to generate CSV reports from saved Discover sessions in Discover.
- Grants access to generate PDF reports in Canvas.
- Grants access to generate PNG and PDF reports in Visualize Library.
If you are using an external identity provider, such as LDAP or Active Directory, you can assign roles to individual users or groups of users. Role mappings are configured in config/role_mapping.yml.
For example, assign the kibana_admin and custom_reporting_user roles to the Bill Murray user:
kibana_admin:
- "cn=Bill Murray,dc=example,dc=com"
custom_reporting_user:
- "cn=Bill Murray,dc=example,dc=com"
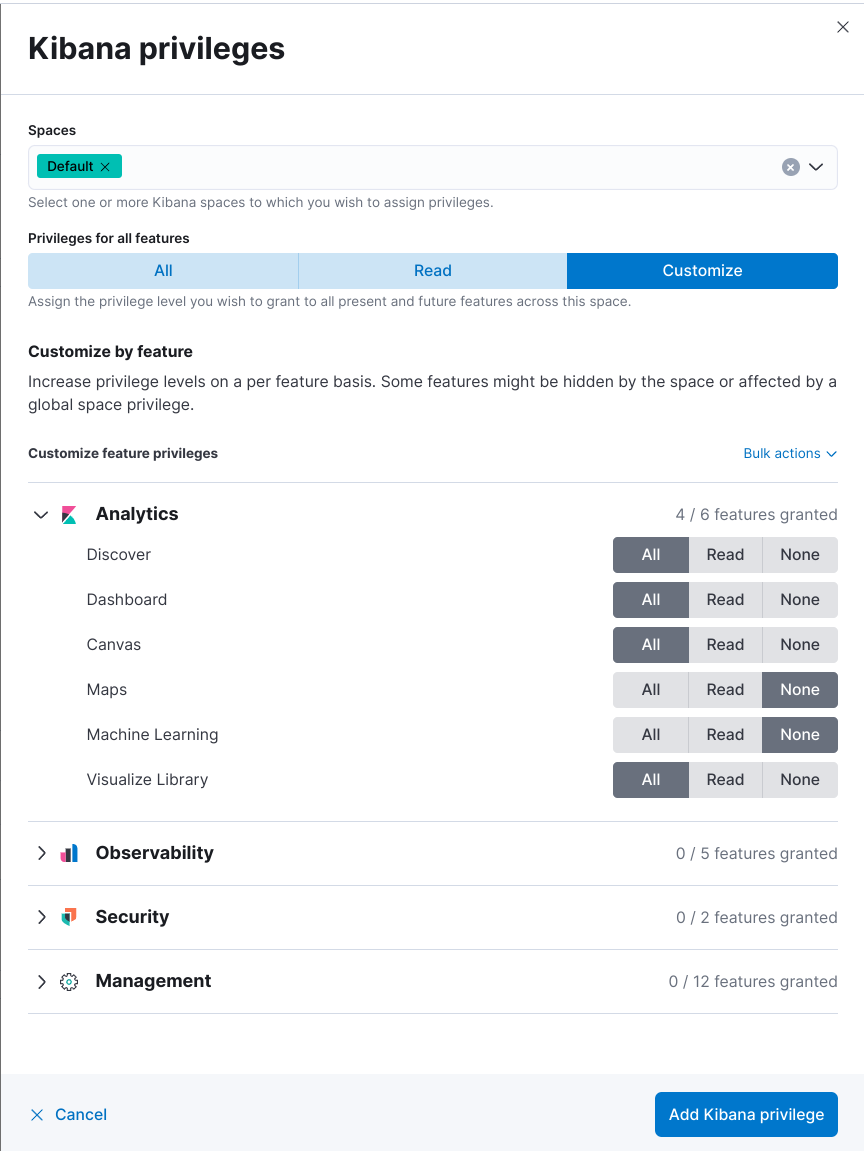
With a Basic license, sub-feature application privileges are unavailable, requiring you to select All privileges for the applications where users can create reports. You can grant users access through the Kibana UI or role API.
Example using Kibana UI:
Example using role API to grant access to CSV reporting features:
PUT localhost:5601/api/security/role/custom_reporting_user
{
"elasticsearch": { "cluster": [], "indices": [], "run_as": [] },
"kibana": [
{
"base": [],
"feature": {
"dashboard_v2": [ "all" ],
"discover_v2": [ "all" ],
},
"spaces": [ "*" ]
}
],
"metadata": {}
}
- Grants access to generate CSV reports from saved Discover sessions in Discover.
- Grants access to generate CSV reports from saved Discover session panels in Dashboard.
- Optional
The following configurations are required at Elasticsearch, Kibana, and OS levels to support reporting features.
These steps apply only to self-managed deployments. Orchestrated deployments include this configuration by default. For more details on different deployment options, refer to Deploy.
To automatically generate reports with Watcher, you must configure Watcher to trust the Kibana server certificate.
Enable Elastic Stack security features on your Elasticsearch cluster. For more information, see Security.
Configure TLS/SSL encryption for the Kibana server. For more information, see Encrypt TLS communications in Kibana.
Specify the Kibana server CA certificate chain in
elasticsearch.yml:If you are using your own CA to sign the Kibana server certificate, then you need to specify the CA certificate chain in Elasticsearch to properly establish trust in TLS connections between Watcher and Kibana. If your CA certificate chain is contained in a PKCS #12 trust store, specify it like so:
xpack.http.ssl.truststore.path: "/path/to/your/truststore.p12" xpack.http.ssl.truststore.type: "PKCS12" xpack.http.ssl.truststore.password: "optional decryption password"Otherwise, if your CA certificate chain is in PEM format, specify it like so:
xpack.http.ssl.certificate_authorities: ["/path/to/your/cacert1.pem", "/path/to/your/cacert2.pem"]For more information, see the Watcher HTTP TLS/SSL Settings.
Add one or more users who have access to the reporting features.
Once you’ve enabled SSL for Kibana, all requests to the reporting endpoints must include valid credentials.
For more information on sharing reports, direct links, and more, refer to Reporting and sharing.
If using PNG/PDF reporting features, make sure the Kibana server operating system has the appropriate packages installed for the distribution.
If you are using RHEL operating systems, install the following packages:
xorg-x11-fonts-100dpixorg-x11-fonts-75dpixorg-x11-utilsxorg-x11-fonts-cyrillicxorg-x11-fonts-Type1xorg-x11-fonts-miscvlgothic-fontsfontconfigfreetype
If you are using Ubuntu/Debian systems, install the following packages:
fonts-liberationlibfontconfig1libnss3
The screenshotting plugin used for reporting features has a built-in utility to check for common issues, such as missing dependencies. See Reporting diagnostics for more information.
If using PNG/PDF reporting features in a production environment, it is preferred to use the setting of server.host: 0.0.0.0 in the kibana.yml configuration file. This allows the headless browser used for PDF/PNG reporting to reach Kibana over a local interface, while also allowing the Kibana server to listen on outward-facing network interfaces, as it makes the Kibana server accessible from any network interface on the machine. Make sure that no firewall rules or other routing rules prevent local services from accessing this address.
Reporting relies on Elasticsearch to install a mapping template for the data stream that stores reports. Ensure that Elasticsearch allows built-in templates to be installed by keeping the stack.templates.enabled setting at the default value of true. For more information, see Index management settings.