It is time to say goodbye: This version of Elastic Cloud Enterprise has reached end-of-life (EOL) and is no longer supported.
The documentation for this version is no longer being maintained. If you are running this version, we strongly advise you to upgrade. For the latest information, see the current release documentation.
Private link traffic filters
editPrivate link traffic filters
editTraffic filtering, to only AWS PrivateLink connections, is one of the security layers available in Elastic Cloud Enterprise. It allows you to limit how your deployments can be accessed.
Read more about Traffic Filtering for the general concepts behind traffic filtering in Elastic Cloud Enterprise.
Private link filtering is supported only for AWS regions. AWS does not support cross-region private link connections. Your private link endpoint needs to be in the same region as your target deployments. Additional details can be found in the AWS VPCE Documentation. AWS interface VPC endpoints get created in availability zones (AZ). In some regions, our VPC endpoint service is not present in all the possible AZs that a region offers. See interface endpoint availability zone considerations for more details.
Transport client is not supported over private link connections.
AWS PrivateLink establishes a secure connection between two AWS Virtual Private Clouds (VPCs). The VPCs can belong to separate accounts, i.e. a service provider and its service consumers. AWS routes the PrivateLink traffic within the AWS data center and never exposes it to the public internet. In such a configuration, Elastic Cloud is the third-party service provider and the customers are service consumers.
Private link is a connection between a VPC Endpoint and a PrivateLink Service.
The process of setting up the Private link connection to your clusters is split between AWS (e.g. by using AWS console) and Elastic Cloud UI. These are the high-level steps:
| AWS console | Elastic Cloud |
|---|---|
1. Create a VPC endpoint using Elastic Cloud service name. |
|
2. Create a DNS record pointing to the VPC endpoint. |
|
3. Create a Private Link rule set with your VPC endpoint ID. |
|
4. Associate the Private Link rule set with your deployments. |
|
5. Interact with your deployments over Private Link. |
Create your VPC endpoint and DNS entries in AWS
edit-
Create a VPC endpoint in your VPC using the service name for your region.
Follow the AWS instructions for details on creating a VPC interface endpoint to an endpoint service.
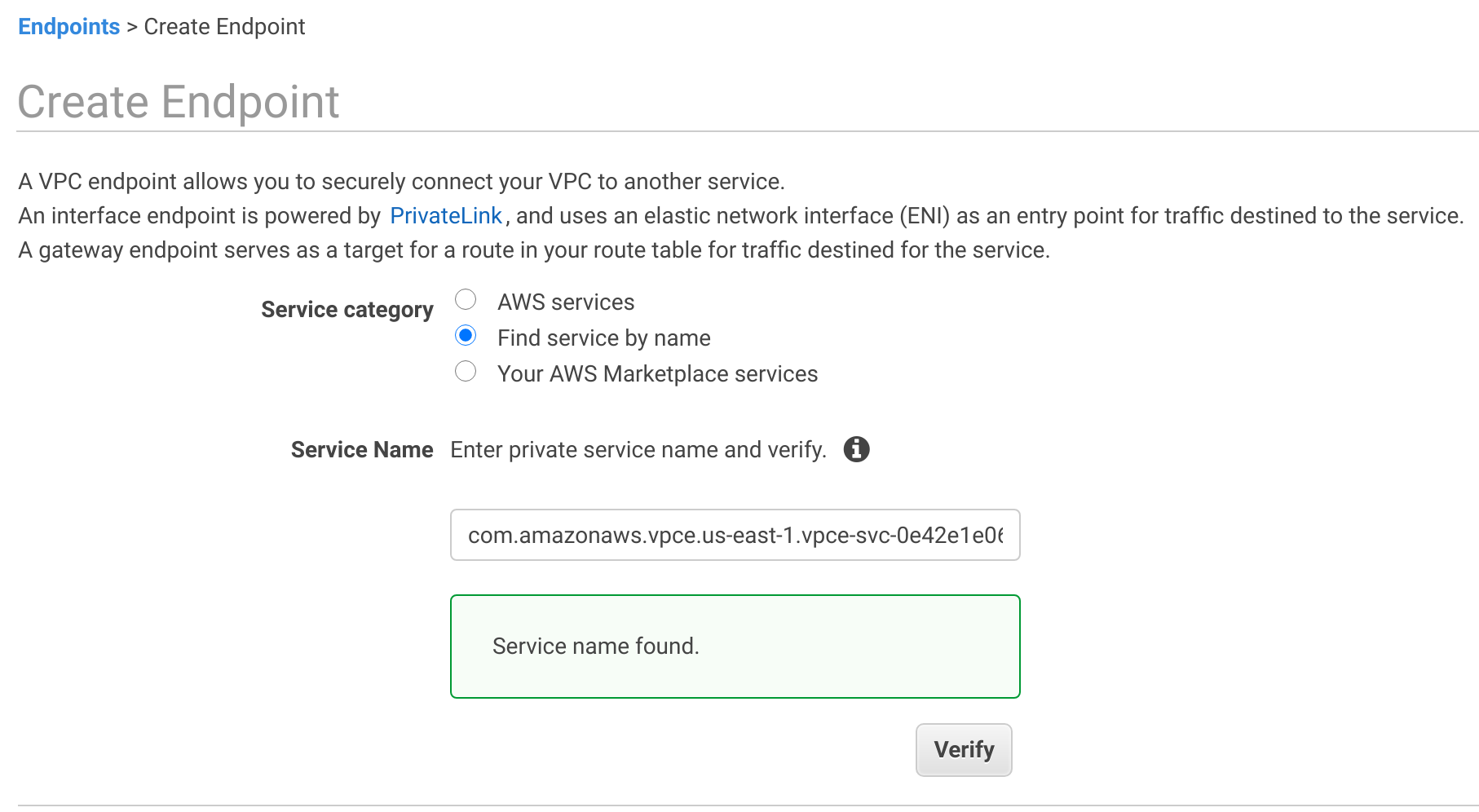
-
Create a DNS record.
-
Create a Private hosted zone. Consult Private hosted zone domain name in Private Link service names and aliases for the name of the zone. For example, in us-east-1 use
vpce.us-east-1.aws.elastic-cloud.comas the zone domain name. Don’t forget to associate the zone with your VPC.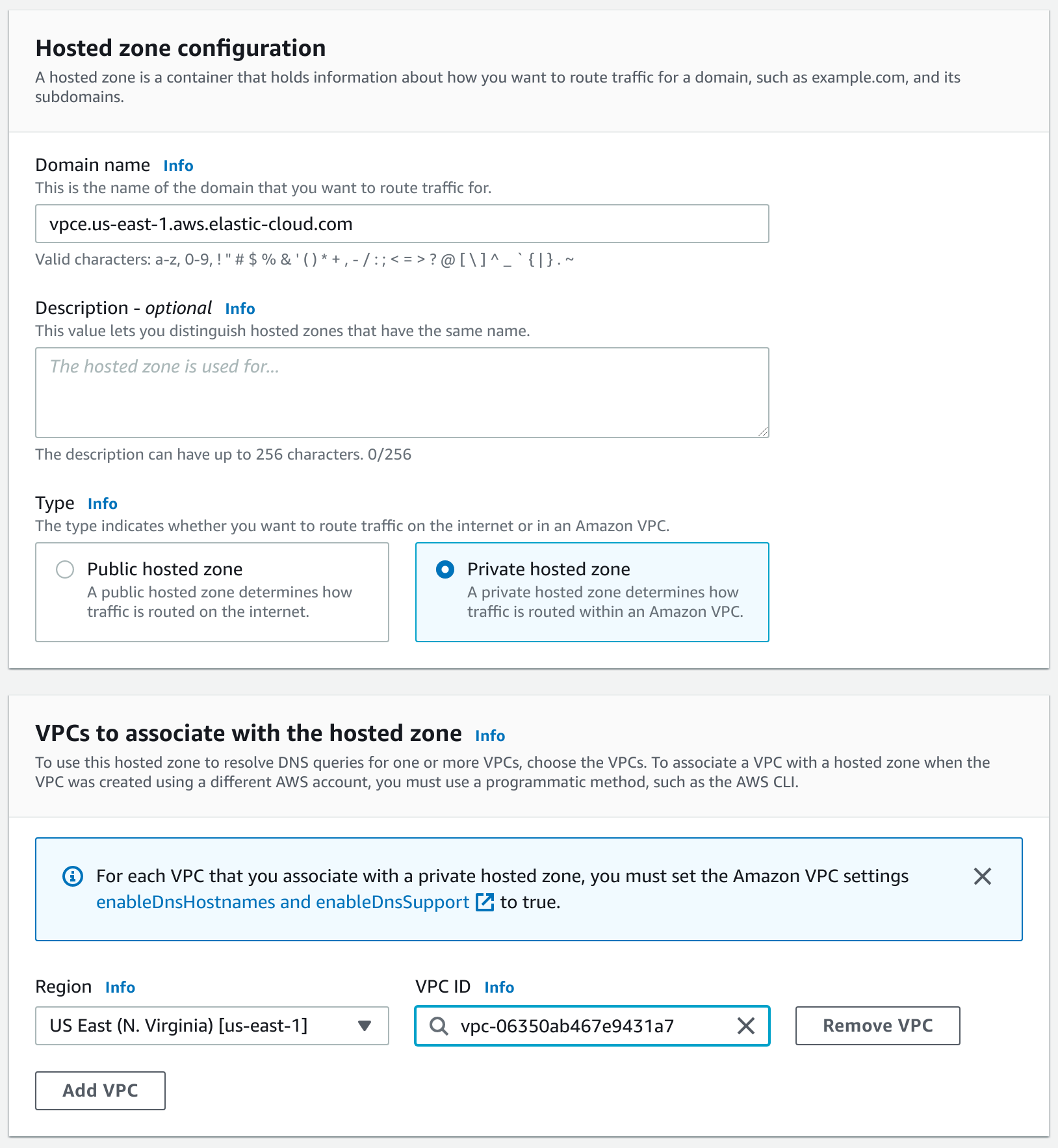
-
Then create a DNS CNAME alias pointing to the PrivateLink Endpoint. Add the record to a private DNS zone in your VPC. Use
*as the record name, and the VPC endpoint DNS name as a value.Follow the AWS instructions for details on creating a CNAME record which points to your VPC endpoint DNS name.
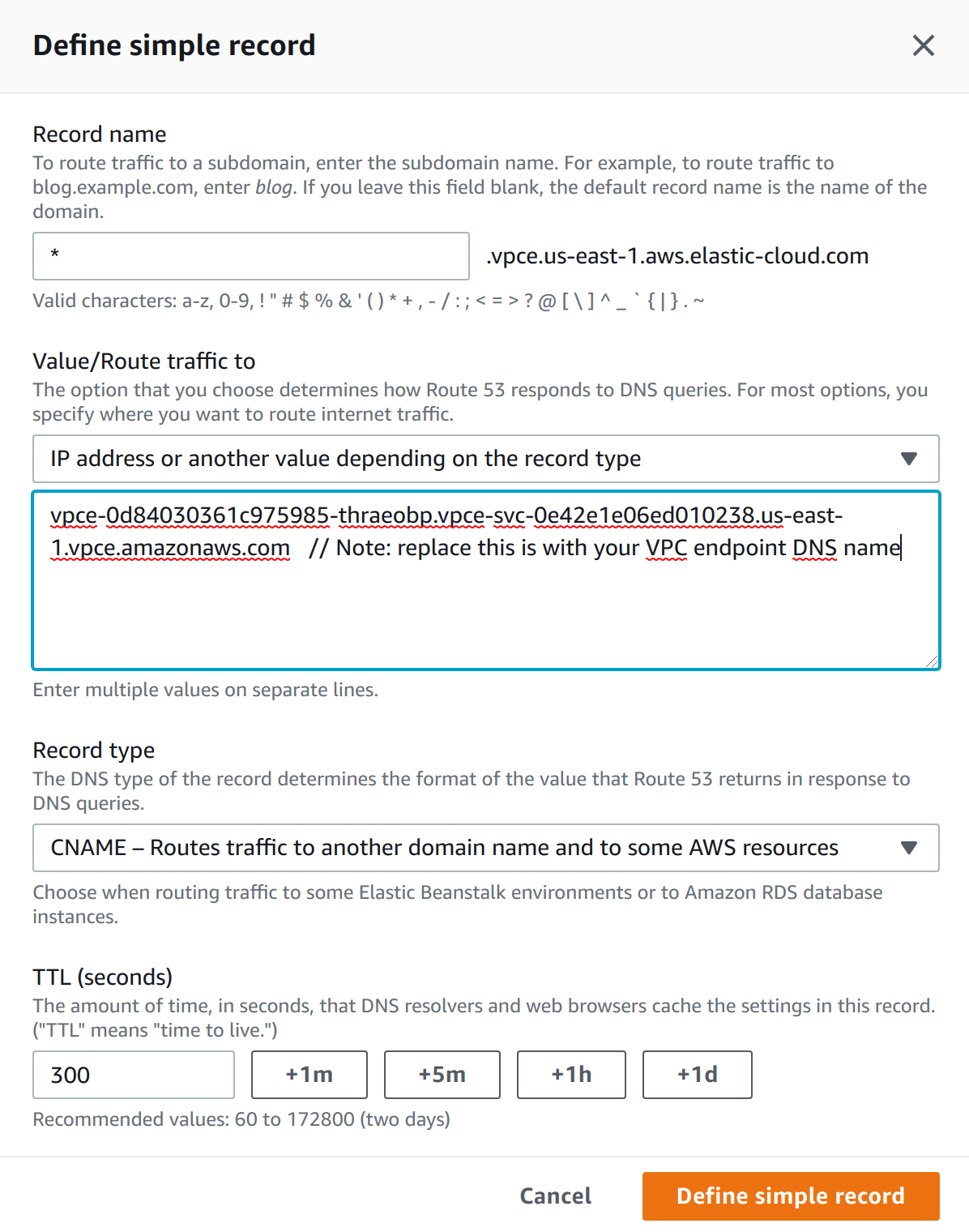
-
-
Test the connection.
Find out the Elasticsearch ID of your deployment. You can do that by clicking Copy endpoint link in the Cloud UI and noting down the first alphanumeric part of the endpoint. For example, if your Elasticsearch endpoint is
https://9c794b7c08fa494b9990fa3f6f74c2f8.us-east-1.aws.found.io:9243then your Elasticsearch ID is9c794b7c08fa494b9990fa3f6f74c2f8.The endpoint ID is different from the deployment ID featured prominently in the user console.
To access your Elasticsearch cluster over Private Link, use the following URL structure:
https://{elasticsearch_ID}.{private_hosted_zone_domain_name}:9243For example:
https://9c794b7c08fa494b9990fa3f6f74c2f8.vpce.us-east-1.aws.elastic-cloud.com:9243You can test the AWS console part of the setup with a following curl (substitute the region and Elasticsearch ID with your cluster):
$ curl -v https://9c794b7c08fa494b9990fa3f6f74c2f8.vpce.us-east-1.aws.elastic-cloud.com:9243 .. * SSL connection using TLS1.2 / ECDHE_RSA_AES_256_GCM_SHA384 * server certificate verification OK * common name: *.vpce.elastic-cloud.com (matched) .. < HTTP/1.1 403 Forbidden {"ok":false,"message":"Forbidden"}The connection is established, and a valid certificate is presented to the client. The
403 Forbiddenis expected, because you haven’t allowed the traffic over this Private Link connection yet.
Add the private link rules to your deployments
editFollow these high-level steps to add private link rules to your deployments.
Finding your VPC endpoint ID
editHaving trouble finding your VPC endpoint ID? You can find it in the AWS console.
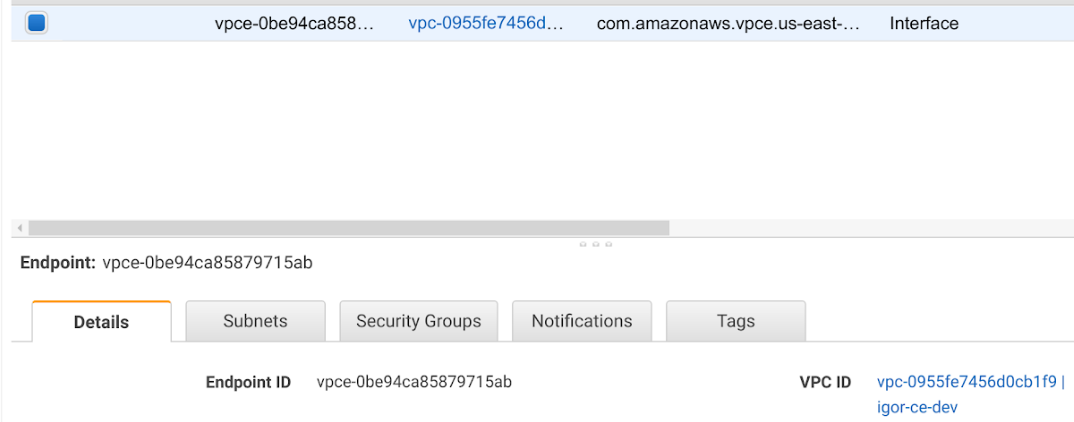
Create rules with the VPC endpoint
editOnce you know your VPC endpoint ID you can create a Private Link traffic filter rule set.
- Log into the Cloud UI.
- From the Platform menu, select Security.
- Click Create filter.
- Select Private link endpoint.
- Create your rule set, providing a meaningful name and description.
- Enter you VPC endpoint ID.
-
Select if this rule set should be automatically attached to new deployments.
Each rule set is bound to a particular region and can be only assigned to deployments in the same region.
The next step is to associate the rule set with your deployments.
Associate a Private Link rule set with your deployment
editTo associate a Private Link rule set with your deployment:
- Go to the deployment.
- On the Security page, under Traffic filters click Apply filter.
- Select the filter you want to apply and click Apply filter.
Access the deployment over private link
editFor traffic to connect with the deployment over a private link, the client making the request needs to be located within the VPC where you’ve created the VPC endpoint. You can also setup network traffic to flow through the originating VPC from somewhere else, such as another VPC or VPN from your corporate network. This assumes that the VPC endpoint and the DNS record are also available within that context. See your service provider documentation for setup instructions.
Use the alias you’ve set up as CNAME DNS record to access your deployment.
If your elasticsearch ID is 9c794b7c08fa494b9990fa3f6f74c2f8 and it is located in us-east-1 region you can access it under https://9c794b7c08fa494b9990fa3f6f74c2f8.us-east-1.aws.found.io:9243.
$ curl -u 'username:password' -v https://9c794b7c08fa494b9990fa3f6f74c2f8.vpce.us-east-1.aws.elastic-cloud.com:9243 .. < HTTP/1.1 200 OK ..
Edit a Private Link connection
editYou can edit a rule set name or to change the VPC endpoint ID.
- Log into the Cloud UI.
- From the Platform menu, select Security.
- Find the rule set you want to edit.
- Click the Edit icon.
Delete a private link rule set
editIf you need to remove a rule set, you must first remove any associations with deployments.
To delete a rule set with all its rules:
- Remove any deployment associations.
- From the Platform menu, select Security.
- Find the rule set you want to edit.
- Click the Remove icon. The icon is inactive if there are deployments assigned to the rule set.
Remove a Private link rule set association from your deployment
editTo remove an association through the UI:
- Go to the deployment.
- On the Security page, under Traffic filters click Remove.