System Module
editSystem Module
editThis functionality is in beta and is subject to change. The design and code is less mature than official GA features and is being provided as-is with no warranties. Beta features are not subject to the support SLA of official GA features.
The system module collects various security related information about
a system. All datasets send both periodic state information (e.g. all currently
running processes) and real-time changes (e.g. when a new process starts
or stops).
The module is fully implemented for Linux. Some datasets are also available for macOS (Darwin) and Windows.
How it works
editEach dataset sends two kinds of information: state and events.
State information is sent periodically and (for some datasets) on startup.
A state update will consist of one event per object that is currently
active on the system (e.g. a process). All events belonging to the same state
update will share the same UUID in event.id.
The frequency of state updates can be controlled for all datasets using the
state.period configuration option. Overrides are available per dataset.
The default is 12h.
Event information is sent as the events occur (e.g. a process starts or stops).
All datasets are currently using a poll model to retrieve their data.
The frequency of these polls is controlled by the period configuration
parameter.
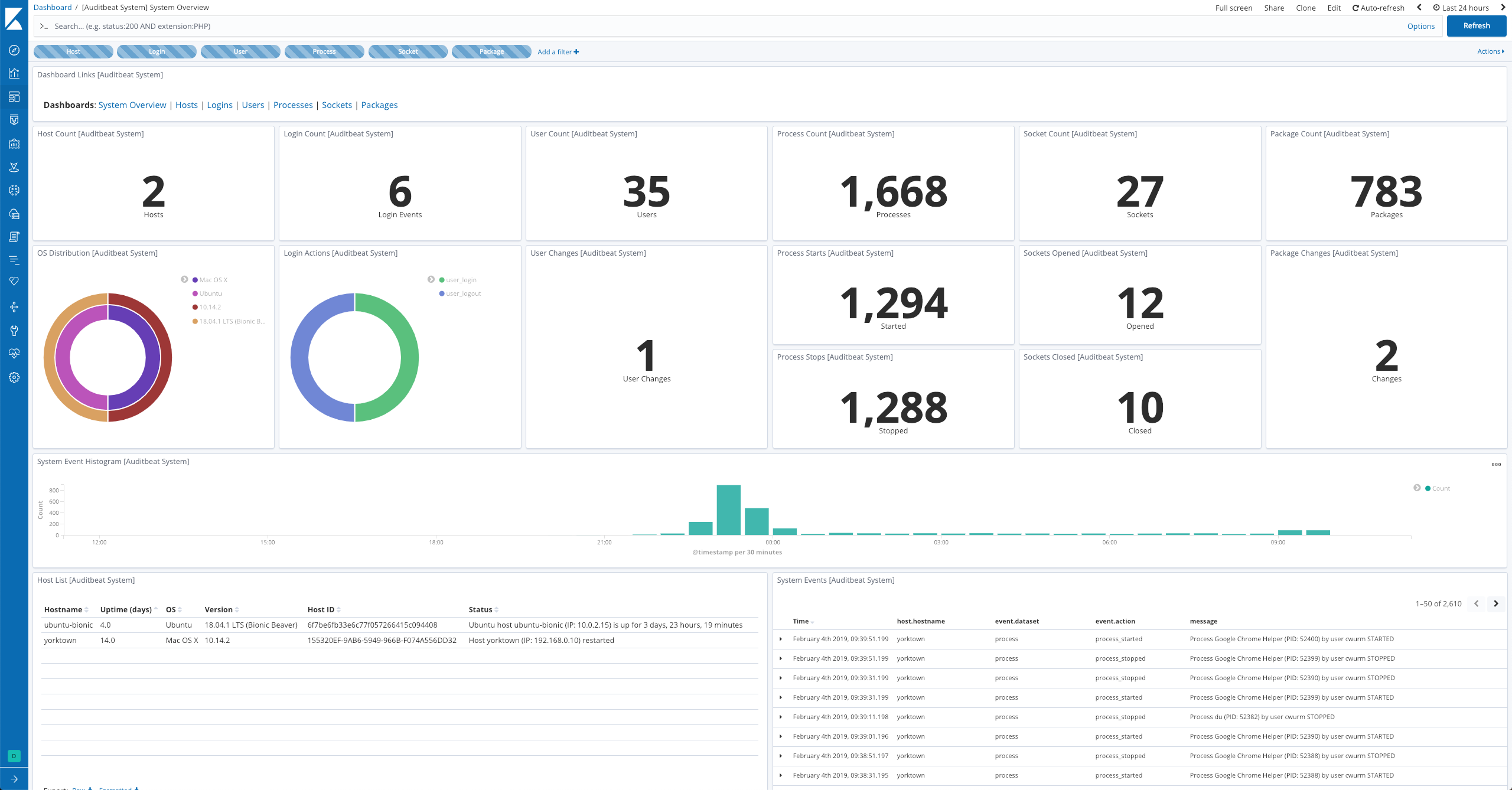
Example dashboard
editThe module comes with a sample dashboard:
Configuration options
editThis module has some configuration options for controlling its behavior. The following example shows all configuration options with their default values for Linux.
It is recommended to configure some datasets separately. See below for a sample suggested configuration.
- module: system
datasets:
- host
- login
- package
- process
- socket
- user
period: 10s
state.period: 12h
socket.include_localhost: false
user.detect_password_changes: true
-
period -
The frequency at which the datasets check for changes. For most
datasets - esp.
processandsocket- a shorter period is recommended. -
state.period -
The frequency at which the datasets send full state information.
This option can be overridden per dataset using
{dataset}.state.period. -
socket.include_localhost -
If the
socketdataset is configured and this option is set totrue, Auditbeat will include sockets that have localhost as either their source and/or destination IP. Defaults tofalse. -
user.detect_password_changes -
If the
userdataset is configured and this option is set totrue, Auditbeat will read password information in/etc/passwdand/etc/shadowto detect password changes. A hash will be kept locally in thebeat.dbfile to detect changes between Auditbeat restarts. Thebeat.dbfile should be readable only by the root user and be treated similar to the shadow file itself.
Suggested configuration
editProcesses and sockets can be short-lived, so the chance of missing an update increases if the polling interval is too large.
On the other hand, host and user information is unlikely to change frequently, so a longer polling interval can be used.
- module: system
datasets:
- host
- login
- package
- user
period: 1m
user.detect_password_changes: true
- module: system
datasets:
- process
- socket
period: 1s
Example configuration
editThe System module supports the common configuration options that are described under configuring Auditbeat. Here is an example configuration:
auditbeat.modules:
- module: system
datasets:
- host # General host information, e.g. uptime, IPs
- login # User logins, logouts, and system boots.
- package # Installed, updated, and removed packages
- process # Started and stopped processes
- socket # Opened and closed sockets
- user # User information
# How often datasets send state updates with the
# current state of the system (e.g. all currently
# running processes, all open sockets).
state.period: 12h
# Enabled by default. Auditbeat will read password fields in
# /etc/passwd and /etc/shadow and store a hash locally to
# detect any changes.
user.detect_password_changes: true
# File patterns of the login record files.
login.wtmp_file_pattern: /var/log/wtmp*
login.btmp_file_pattern: /var/log/btmp*
Datasets
editThe following datasets are available: