Use Synthetics with traffic filters
editUse Synthetics with traffic filters
editIf you are setting up Synthetics for a deployment configured with traffic filters, none of your results will be visible in the Synthetics app until permission to write the results to Elasticsearch is explicitly granted.
If you don’t configure the traffic filters, the tests will run, but in the UI it will appear like they are not running because the results cannot be written back to Elasticsearch.
Obtain the IP address
editThe IP address or CIDR block of the hosts running the tests need to be configured in your Traffic filters to allow inbound connection into your Elasticsearch instance to store the results.
The IP addresses to be used depend on where the monitors are running, either on Elastic’s global managed testing infrastructure or Private Locations.
Elastic’s global managed testing infrastructure
editIf you’re running tests on Elastic’s global managed testing infrastructure, you can find the relevant IP CIDR block (a single address or /32 block for each region) in this list of egress IPs. This list is a JSON object that contains each region in Elastic’s global managed testing infrastructure and the address that outbound connections will be made from. These will be the connections into your Elasticsearch cluster.
For example, the Europe - United Kingdom region has the following entry:
"europe-west2-a": {
"ip_prefix": ["34.89.88.187/32"],
"name": "Europe - United Kingdom"
}
To run tests from the Europe - United Kingdom region, you need to enable access
from the 34.89.88.187/32 CIDR block.
Note that as regions are added, this list will change. Similarly existing region addresses are subject to change.
Private Locations
editIf you’re running tests from Private Locations, you will have the Elastic Agent installed on host machines that run the tests. You need to obtain the address ranges for these machines. This needs to be the IP address that the host is making the connection from into the Elasticsearch cluster. This might not be the IP address bound to the network interface of the host machine, but the proxy or other address based on your network configuration.
Add the traffic filter
editOnce you know the CIDR blocks for your testing sources, add them to your Elasticsearch deployment. Find detailed instructions in the IP traffic filters docs.
For example, if you had a Private Location running with a public CIDR block of 1.2.3.4/32
and were running tests from the Europe - United Kingdom region,
you would first create a traffic filter with the following:
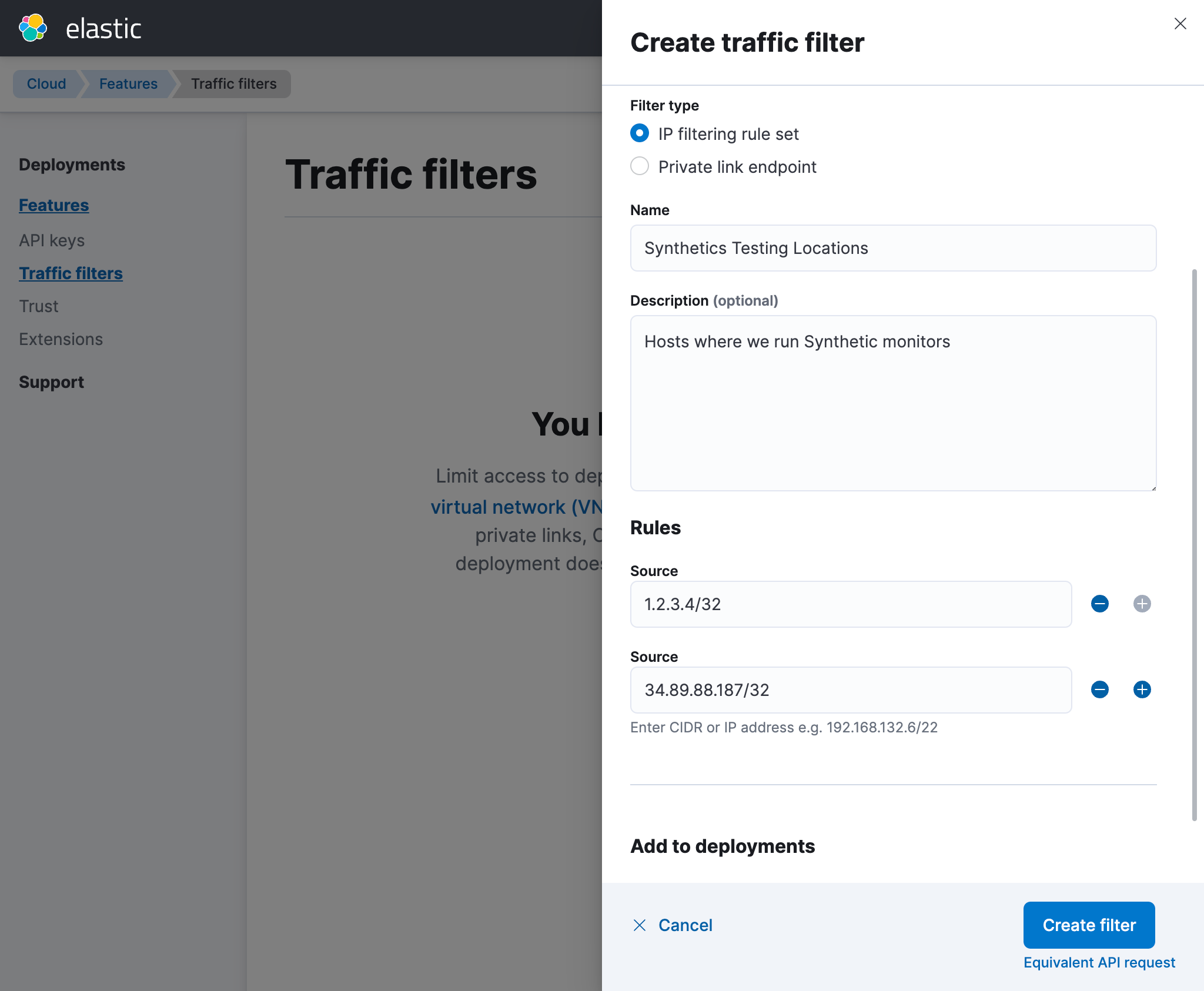
Once the traffic filter has been created, it needs to be assigned to the deployment from which you’re managing monitors from (the deployment containing the Elasticsearch cluster where your results need to go).