Roles and privileges
Use Kibana roles and privileges to grant users access to Fleet and Integrations. Fleet and integrations privileges can be set to:
all- Grants full read-write access.
read- Grants read-only access.
none- No access is granted.
You can take advantage of these privilege settings by:
To configure access at a more granular level, select a custom set of privileges for individual Fleet features:
Elasticsearch comes with built-in roles that include default privileges.
editor-
The built-in
editorrole grants these privileges, supporting full read-write access to Fleet and Integrations:- Fleet:
all - Integrations:
all
- Fleet:
viewer- The built-in
viewerrole grants these privileges, supporting read-only access to Fleet and Integrations:
- Fleet::
read - Integrations::
read
You can also create a new role that can be assigned to a user, in order to grant more specific levels of access to Fleet and Integrations.
To create a new role with access to Fleet and Integrations:
In Kibana, go to Management → Stack Management.
In the Security section, select Roles.
Select Create role.
Specify a name for the role.
Leave the Elasticsearch settings at their defaults, or refer to Security privileges for descriptions of the available settings.
In the Kibana section, select Assign to space.
In the Spaces menu, select All Spaces. Because many Integrations assets are shared across spaces, users need the Kibana privileges in all spaces.
Expand the Management section.
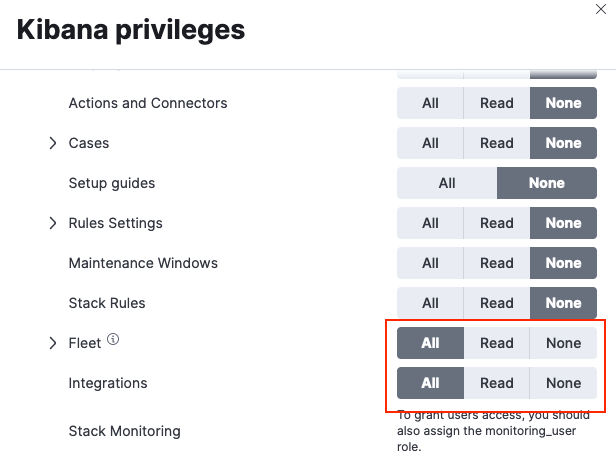
Set Fleet privileges to All.
Choose the access level that you'd like the role to have with respect to Fleet and integrations:
- To grant the role full access to use and manage Fleet and integrations, set both the Fleet and Integrations privileges to
All.
- To create a read-only user for Fleet and Integrations, set both the Fleet and Integrations privileges to
Read.
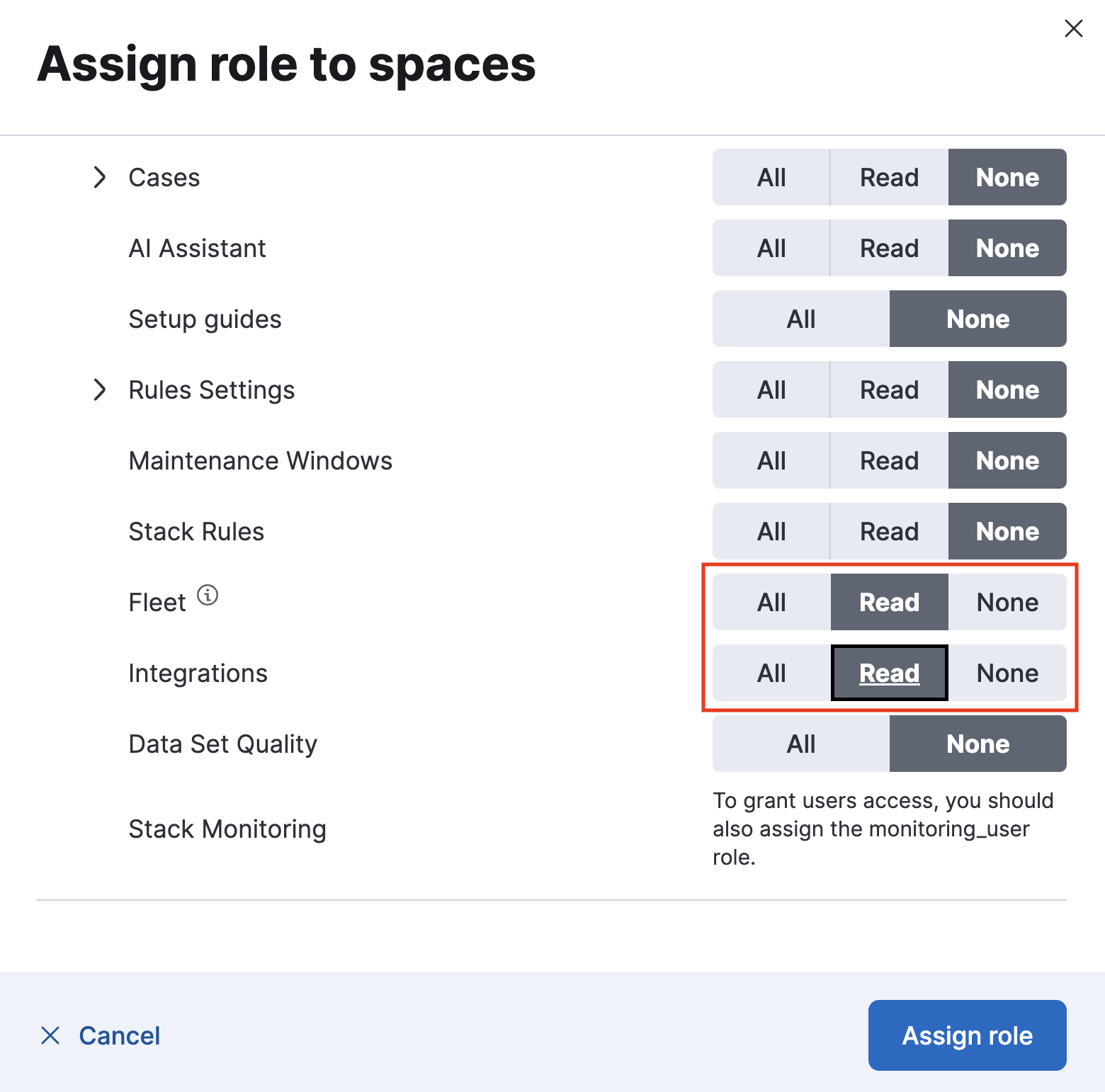
- If you'd like to define more specialized access to Fleet based on individual components, expand the Fleet menu and enable Customize sub-feature privileges.
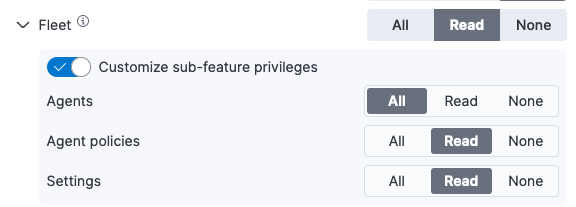
Any setting for individual Fleet components that you specify here takes precedence over the generalAll,Read, orNoneprivilege set for Fleet.Based on your selections, access to features in the Fleet UI are enabled or disabled for the role. Those details are covered in the next section: Customize access to Fleet features.
- To grant the role full access to use and manage Fleet and integrations, set both the Fleet and Integrations privileges to
After you've created a new role, you can assign it to any Elasticsearch user. You can edit the role at any time by returning to the Roles page in Kibana.
Beginning with Elastic Stack version 9.1, you have more granular control when creating a new role or editing it. This is useful when people in your organization access Fleet for different purposes, and you need to fine-tune the components that they can view and the actions that they can perform.
The Fleet UI varies depending on the privileges granted to the role.
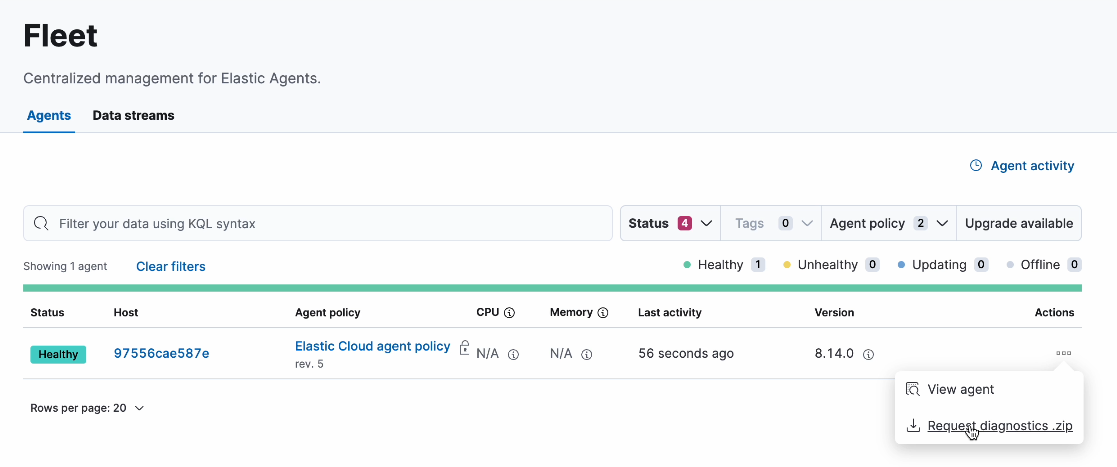
Set Read access for Elastic Agents only:
- Agents:
Read - Agent policies:
None - Settings:
None
With these privileges, the Fleet UI shows only the Agents and Data streams tabs. The Agent policies, Enrollment tokens, Uninstall tokens, and Settings tabs are unavailable.
The set of actions available for an agent are limited to viewing the agent and requesting a diagnostics bundle.
Change the Agents privilege to All to enable the role to perform the full set of available actions on Elastic Agents.
Set Read access for Elastic Agents, agent policies, and Fleet settings:
- Agents:
Read - Agent policies:
Read - Settings:
Read
With these privileges, the Fleet UI shows the Agents, Agent policies, Data streams, and Settings tabs. The Enrollment tokens and Uninstall tokens tabs are unavailable.
The set of actions available for an agent are limited to viewing the agent and requesting a diagnostics bundle.
You can view agent policies, but you cannot create a new policy.
You can view Fleet settings, but they are not editable.
Set All access for Elastic Agents only:
- Agents:
All - Agent policies:
Read - Settings:
Read
With these privileges, the Fleet UI shows all tabs.
All Elastic Agent actions can be performed and new agents can be created. Enrollment tokens and uninstall tokens are both available.
Access to Fleet settings is still read-only.
To enable actions such as creating a new Fleet Server, set the Fleet Settings privilege to All.
This table shows the set of available actions for the read or all privilege for each Fleet feature.
| Component | read privilege |
all privilege |
|---|---|---|
| Agents | View-only access to Elastic Agents, including: * View a list of all agents and their status * Request agent diagnostic packages |
Full access to manage Elastic Agents, including: * Perform upgrades * Configure monitoring * Migrate agents to a new cluster * Unenroll agents from Fleet * Set the inactivity timeout * Create and revoke enrollment tokens |
| Agent policies | View-only access, including: * Agent policies and settings * The integrations associated with a policy |
Full access to manage agent policies, including: * Create a policy * Add an integration to a policy * Apply a policy * Edit or delete an integration * Copy a policy * Edit or delete a policy * Change the output of a policy |
| Fleet settings | View-only access, including: * Configured Fleet hosts * Fleet output settings * The location to download agent binaries |
Full access to manage Fleet settings, including: * Editing hosts * Adding or editing outputs * Update the location for downloading agent binaries |