It is time to say goodbye: This version of Elastic Cloud Enterprise has reached end-of-life (EOL) and is no longer supported.
The documentation for this version is no longer being maintained. If you are running this version, we strongly advise you to upgrade. For the latest information, see the current release documentation.
Inbound traffic
editInbound traffic
editWhen there are multiple hosts for each role, the inbound networking and ports can be represented by the following diagram:
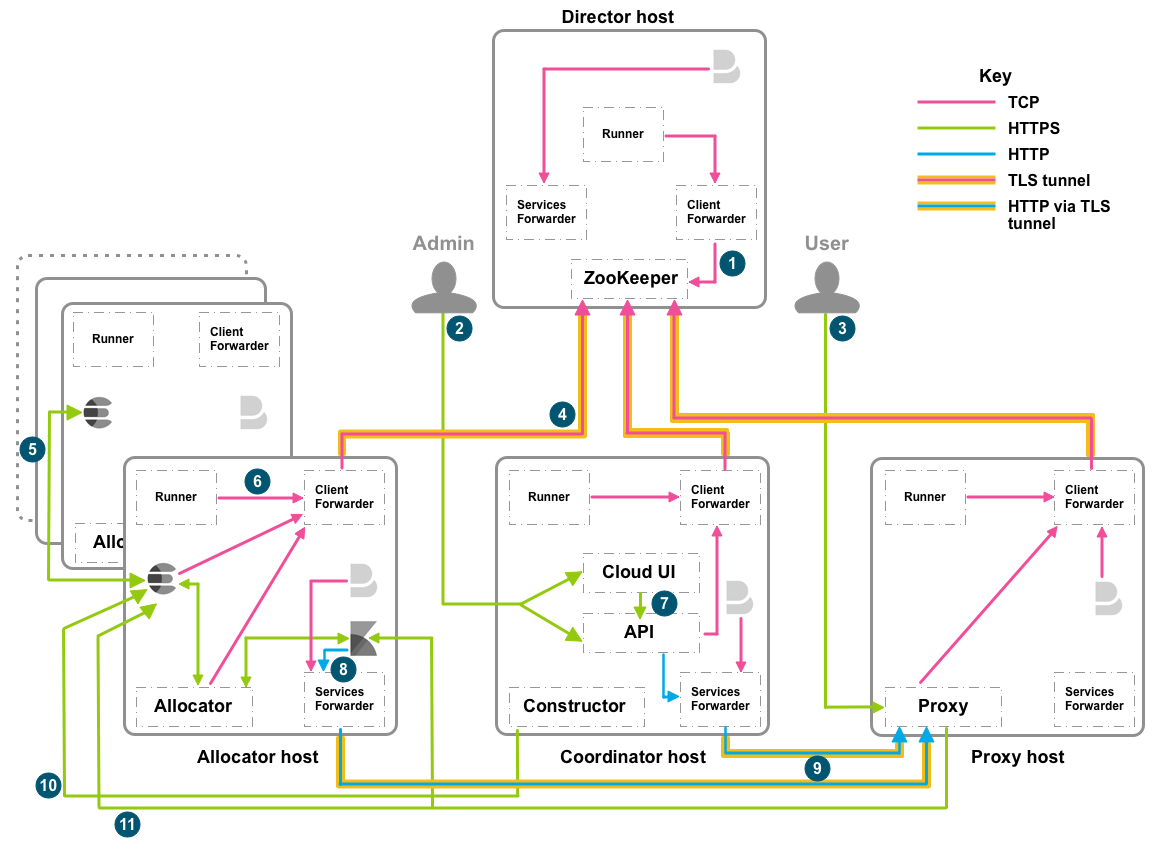
Inbound traffic from any source
edit| Number | Host role | Inbound ports | *Purpose* |
|---|---|---|---|
All |
22 |
Installation and troubleshooting SSH access only (TCP) |
|
2 |
Coordinator |
12300/12343, 12400/12443 |
Admin API access (HTTP/HTTPS) |
3 |
Proxy |
9200/9243, 9300/9343 |
Elasticsearch (transport client/transport client with TLS/SSL), also required by load balancers |
7 |
Coordinator |
12400/12443 |
Cloud UI console to API (HTTP/HTTPS) |
Inbound traffic from internal components of ECE
editIn addition to the following list, you should open 12898-12908 and 13898-13908 on the director host for Zookeeper leader and election activity.
| Number | Host role | Inbound ports | *Purpose* |
|---|---|---|---|
1 |
Director |
2112 |
ZooKeeper ensemble discovery/joining (TCP) |
4 |
Director |
12191-12201 |
Client forwarder to ZooKeeper, one port per director (TLS tunnels) |
5 |
Allocator |
19000-19999 |
Elasticsearch node to node (Node Transport 6.x+/TLS 6.x+) |
6 |
Allocator |
18000-18999/20000-20999 |
Proxy to Elasticsearch/Kibana/APM Server instance (HTTPS/Transport Client 6.x+/TLS 6.x+) |
7 |
Coordinator |
22191-22195 |
Connections to initial coordinator from allocators and proxies, one port per coordinator, up to five (TCP) |
8 |
Allocator |
9244 |
Kibana to the services forwarder (HTTP) |
9 |
Proxy |
9200/9243, 9300/9343 |
Kibana and Elasticsearch (HTTP via TLS tunnel) |
10 |
Allocator |
18000-18999 |
Constructor to Elasticsearch cluster (HTTPS) |
11 |
Allocator |
18000-18999/20000-20999 |
Elasticsearch (HTTPS/Transport Client TLS) |
12 |
Allocator |
21000-21999 |
APM Server (Instance Monitoring) |
13 |
Proxy |
9000/9043 |
Proxy metrics endpoint (HTTP/HTTPS) |
If you have IP filtering set up for your deployment, make sure to create rule sets the IP addresses that you need. All other inbound traffic will be blocked. Internal deployment traffic between Kibana instances, APM Servers, and the Elasticsearch clusters is automatically allowed.